- D/A
- Digital to Analog. See DAC.
- DAB
- Digital Audio Broadcasting. A European standard for digital commercial FM radio. It broadcasts at 174 to 240 MHz RF.
- DAC
- Digital-to-Analog Converter. A device that converts bits into analog signals or waveforms.
- daemon
- In Unix and related operating systems, a program that’s always running in the background to respond to service requests. The Windows service is equivalent.
- D-AMPS
- Digital AMPS. See AMPS, IS-136.
- DAO
- (1)
- Data Access Object. A Microsoft data-access technology.
- (2)
- Department/Agency/Organization. See STU.
- (3)
- Decentralized Autonomous Organization. An online group that shares decision-making ability based on shares of cryptocurrency or NFTs.
- DAQ
- Data Acquisition. A widely used family of data-capture hardware & software modules created by National Instruments. See LabVIEW.
- dark matter
- A mysterious substance thought by physicists to make up about 27% of the mass of the universe. (An even more mysterious something called dark energy supplies another 68%, leaving roughly 5% of the universe for visible matter.) Proposed to explain the glaring differences between predicted and observed movements of distant galaxies, dark matter interacts with gravity but not with the EM fields of visible matter, meaning it can’t be observed directly. Candidates include the axion, a subatomic particle with mass many orders of magnitude less than a proton; the WIMP (weakly interacting massive particle), with mass hundreds of times greater than a proton; and the dark magnetic monopole. Experiments to find evidence of these particles are ongoing.
- Physicists are aware of the comparisons to ether and phlogiston.
- darknet
- Originally, this meant any portion of the Internet’s allocated IP address space containing no servers known to the DNS, hence not indexed or searchable by standard Internet tools. Most of these addresses belong to networks, databases, and servers that need to be online but that aren’t meant for direct or public access. Nowadays, this vast archipelago of unlisted networks is called dark address space, the Dark Internet, or, for just the parts based on HTML, the Deep Web. It’s many, many times the size of the visible World-Wide Web.
- “Darknet” has acquired a more specific meaning: an Internet community within the Dark Internet that’s intentionally hidden from external searches, and that conceals the identities of users and the physical locations of hosts and peer-to-peer nodes. These communities are a mix of users seeking anonymity for whatever reason, and markets for restricted or illegal goods and services. The largest as of 2016 are Tor, Freenet, and I2P. By design, these networks have no administrator or dedicated infrastructure, and no direct way to know who and where other users are. Users access them with custom browsers, which provide encryption and route connections through proxy chains. As with the rest of the Internet, users can set up and run their own servers on a darknet.
- The Darknet, capitalized, refers collectively to all of these hidden networks. They’re also called the Dark Web or the Invisible Web. This imprecise nomenclature invites confusion with similar names for dark address space, obscuring the fact that, in contrast to the latter, the Darknet is far smaller than the visible Web.
- dark pattern
- Behavior built into a software application that tricks or manipulates users into making choices preferred by the designers. For example, ads that put a
Replaybutton where theClosebutton normally goes, and Windows installations that push users to a Microsoft account as their login by hiding the standard local-account option. - DARPA
- Defense Advanced Research Projects Agency. See ARPA.
- DAT
- Digital Audio Tape. Obsolete standard magnetic tape cassette for digitized audio signals sampled at 48 kHz.
- database
- The classic format is the relational database, a 2D array of rows and columns. A new format designed to support intensive analysis is the multidimensional database (aka physical cube), in which each attribute of the data is one dimension in a multidimensional structure, with each data element tied to the intersection of these dimensions. Analysts are then able to produce different 2D views of the database based on criteria of interest (see OLAP). There are also ROLAP (relational OLAP) tools, which perform multidimensional analysis on 2D relational databases. See RDBMS.
- data code
- A type of source coding that uses a fixed set of binary patterns to represent human-readable characters and, in some cases, teletype operations or other control codes. Some examples:
- ANSI – American National Standards Institute. A common misnomer referring to an 8-bit expansion of 7-bit ASCII used on PCs, especially an 8-bit character set in English-language versions of Microsoft Windows. These codes are similar but not identical to the ISO/IEC-8859-1 standard, and are not ANSI standards.
- ASCII – American Standard Code for Information Interchange, pronounced “ASS-kee”. An ANSI standard 7-bit (128-character) code for English. With 8-bit bytes, values 0-31 are control characters, 32-127 are used for text, and 128-255 are unallocated. There are various non-standard, 8-bit ASCII extensions, such as IBM’s OEM character set. In many Windows programs, holding down the Alt key and entering a 4-digit number from 0000 to 0255 types the corresponding ASCII or extended ASCII character. ASCII art refers to images constructed out of ASCII characters.
- Baudot – The most common worldwide in the early 1990s, aka International Code #2. A 5-bit code with 50 characters, a space, and 7 control characters (including shift-up and shift-down symbols).
- DMCS – DEC Multinational Character Set. An 8-bit ASCII extension.
- EBCDIC – Extended Binary-Coded Decimal Interchange Code. Obsolete 8-bit IBM standard.
- IPARS – International Passenger Airline Reservation System. 6-bit.
- ISO/IEC-8859 – A series of 8-bit expansions of 7-bit ASCII created jointly by the ISO and IEC. ISO/IEC-8859-1, the Latin-1 set, supports most West European languages, including English. The other family members are for other linguistic regions.
- SBT – Six-Bit Transcode.
- UCS – Universal Character Set. A superset of all other character set standards, defined by ISO 10646. No information will be lost if you convert any text string to UCS and then back to the original encoding. With 31 bits per character, UCS contains the characters required to represent practically all known languages, and more are being added. The most common character sets are in the range 0x0000 to 0xFFFD, a 16-bit subset called the basic multilingual plane (BMP) or Plane 0. UCS-2 and UCS-4 refer to implementations using 2 bytes and 4 bytes per character, respectively.
- Unicode – A largely US commercial initiative to produce a single, standard, international character set, starting from ASCII. The character set is identical to that of UCS, but Unicode imposes additional constraints to ensure cross-platform consistency, provides algorithms for modifying the presentation forms of certain scripts (e.g. Arabic), specifies handling of bi-directional text (e.g. mixing Latin & Hebrew), etc. Unicode character strings should be preceded by a byte-order mark to specify format (UTF-8, UTF-16, etc.) and big-endian or little-endian. Unicode characters can be typed using the Alt key in the same way that ASCII characters can.
- UTF-# – Unicode (or UCS) Transformation Format. Any of several UCS or Unicode character coding formats. Common ones include UTF-8 (identical to 7-bit, 1-byte ASCII for standard ASCII characters, but uses 2 to 6 bytes for non-ASCII), UTF-16 (2 bytes per character, identical to UCS-2), and UTF-32 (4 bytes, identical to UCS-4). UTF characters can be typed using the Alt key in the same way that ASCII characters can.
- data mining
- An advanced, open-ended way of deriving new information from databases. Rather than asking specific questions, it looks for patterns.
- data protocol
- Rules for the format of a message. Asynchronous protocols can send at irregular intervals with start and stop bits. Synchronous protocols are in sync with a clock – in effect, the data bits are the clock – and use flags or sync characters. Character-oriented protocols (COPs) transmit sync characters, while bit-oriented protocols (BOPs), which are always synchronous, use flags and sync bits.
- The BOP flag is 01111110 or 10000001. BOPS use bit stuffing, and zero insertion after 5 consecutive 1s to prevent false flags. BOPs use three different frame types: information frames, supervisory frames, and unnumbered command/response frames. Information frames consist of a flag, the address field, the control field, the data, a frame check sequence (the CRC), and a terminating flag. Supervisory frames are for message acknowledgement and indicating not-ready-to-receive condition.
- Some common protocols:
- ADLC – Asynchronous Data Link Control. An IBM SNA-compatible protocol for asynchronous connection of remote terminals.
- BISYNC – Binary Synchronous Communications. A half-duplex IBM COP that supports ASCII, EBCDIC, and SBT codes. Messages are sent as one or more blocks of text surrounded by sync, header, and error control characters. It’s been largely replaced by the more efficient SDLC.
- DDCMP – Digital Data Communications (or Control) Message Protocol. DEC’s full-duplex COP that usually carries ASCII or EBCDIC. Like all full-duplex protocols, it sends data in frames (packets): 80 bits of overhead, the message data, and then 24 more bits of overhead.
- HDLC – High-level Data Link Control. A full-duplex BOP nearly identical to SDLC. Each frame opens with an 8-bit flag [01111110], an 8-bit(+) address, and 8 control bits. Then comes the data, then a 16-bit(+) checksum and a closing 8-bit flag. 802.2 and the LAPx protocols are implementations of HDLC.
- IPARS – International Passenger Airline Reservation System. A COP that usually uses 111111 111110 as sync characters. Data is usually inverted and reversed for transmission.
- Kermit – A file transfer protocol developed at Columbia University. It’s designed to handle data exchange between very different computer types, mainly mini-computers and mainframes.
- RTS/CTS – Request to Send/Clear To Send. A hardware flow control protocol for serial communications, e.g. RS-232, between a sending device (DTE) and receiving device (DCE). These are usually a computer and a modem, respectively. The DTE sets the RTS active (active can be defined as either high or low voltage state), the DCE responds by setting CTS active, and the DTE sends a preamble followed by serial data. After the last byte, the DTE sets RTS inactive, and the DCE sets CTS inactive and (typically) sends an ACK or NAK packet. If either end is in danger of a data buffer overflow, it can set its signaling line inactive to direct the other end to pause. Compare this with software flow control such as Xon/Xoff.
- SDLC – Synchronous Data Link Control. A full-duplex BOP for IBM’s SNA network.
- Xmodem – A widely used COP developed in the 1970s for half-duplex file transfer. The original Xmodem uses 128-byte packets, plus a 4-character checksum for error detection. Xmodem-CRC preferentially uses a CRC for error detection. Xmodem-1K is a version of Xmodem-CRC with 1024-byte packets.
- Xon/Xoff – A software flow control protocol for asynchronous serial communications. Xon (the ASCII character CTRL-Q, or 00010011) starts transmission, and Xoff (the ASCII character CTRL-S, or 00010001) stops it. Since a binary data stream might contain these patterns, Xon/Xoff is risky for non-text transmissions.
- Ymodem – A file transfer protocol. It’s identical to Xmodem-1K, except that it supports batch file transfers. Ymodem-g is a streaming protocol that sends 1 kB packets in a continuous stream until directed to stop, and expects the modem to handle error correction.
- Zmodem – A very efficient file transfer protocol. It’s similar to Ymodem-g, but has crash recovery – if a transfer fails, it can be resumed later, and previously sent 1 kB blocks needn’t be re-sent.
- DB
- Database. See database.
- dB
- Decibels. The logarithm of a dimensionless ratio of two signal levels. It’s used to describe gain or loss passing through a system, compare signal to noise, etc. The base unit is actually the bel, named for Scottish-Canadian-American inventor Alexander Graham Bell (1847-1922), but the decibel – 1/10th of a bel – is standard. (That’s where the factor of 10 in the equations comes from.) For voltage comparisons, dB = 20 log [V1/V2], where V1 and V2 are the root mean square (RMS) voltages of the signals being compared. For power, dB = 10 log [P1/P2]. A power gain of 2:1 is 3.01 dB, 10:1 is 10 dB, 100:1 is 20 dB, etc.
- Do not mix dB with regular numbers. If you double 10 dB, for example, that’s not 20 dB, it’s 10 log [2 × 10:1] = 13.01 dB.
- When antenna gain is given in dB, it generally means dBd. RF power is often expressed in dBm or dBW – decibels are more convenient than absolute measures such as watts, because they can be added. Example: An RF stage outputs a 2W signal, which sustains a 0.7 dB cable loss and a 6 dB antenna gain. 2W = 3.01 dBW, so the EIRP from the antenna’s main lobe is 3.01 - 0.7 + 6 = 8.31 dBW, or 6.776 W.
- Some typical sound levels in decibels relative to the sound pressure level (SPL), or dBSPL:
- The typical human pain threshold for noise is somewhere between 132 and 138 dBSPL. Permanent hearing loss can occur from prolonged or repeated exposure to sounds as low as 85 dBSPL.
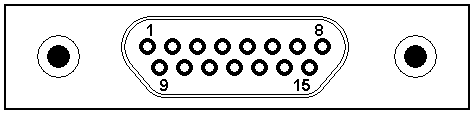
- DB-##
- A member of the D-sub family of cable connectors.
- DBA
- (1)
- Dynamic Bandwidth Allocation.
- (2)
- Database Administrator.
- dBc
- Decibels relative to the signal carrier. See dB.
- dBd
- Decibels of gain relative to that of a lossless half-wave dipole antenna. Sometimes used instead of dBi to specify antenna gain. 2.15 dBi = 0 dBd. See dB.
- dBi
- Decibels relative to a theoretical isotropic radiator, which has a gain of 1.0 in every direction. Used to specify gain of antennas. The value is the same whether transmitting or receiving. See dB, EIRP.
- dBm
- Decibels relative to 1 milliwatt. 1 mW = -3 dBW = 0 dBm. See dB.
- DBMS
- Data Base Management System. They come in the relational and non-relational flavors. See database.
- D-BPSK
- Differential Binary Phase Shift Keying. Identical to BPSK, except for differentially coherent detection at the receiver (which mandates differential source encoding). See DPSK.
- DBR
- Distributed Bragg Reflector. A Bragg grating built into an optical waveguide, including but not limited to optical fiber. A DBR laser has a fiber Bragg grating (FBG) at one end reflecting a particular tuned wavelength, and an exit facet at the other end. Current injected into the gain region close to the facet causes lasing, and the FBG reflects only the target wavelength back toward the exit facet. Unlike the similar distributed feedback (DFB) laser, the DBR laser’s FBG is separate from the gain region to prevent gaps in the tuning range.
- DBS
- Direct Broadcast Satellite. A GEO-based digital satellite TV system in the 10-40 GHz range. As of 2009, the biggest two in the US are Echostar’s DishNetwork and Hughes’s DirecTV. The signals are circular-polarized, and different channels can use different polarities. Thanks to the higher frequency, signal power, etc., they can use much smaller dishes (18-36") than the old BUD, but are more susceptible to rain fade.
- dBSPL
- Decibels Sound Pressure Level. See dB.
- dBW
- Decibels relative to 1 watt. 1 W = 30 dBm = 0 dBW. See dB.
- DC
- Direct Current. Current that flows in one direction only, e.g. battery current.
- AC dominates in the power grid partly because it’s what generators produce, and partly because the transformers to step up AC voltage for transmission and step down AC voltage for distribution are cheaper and more efficient than the rectifiers and (especially) inverters that are needed for DC. However, DC has smaller line loss than AC and requires just two lines, so it’s more economical for some long-distance transmission systems, which are called HVDC (high voltage DC).
- DC power connectors for the much lower voltages used in the world of consumer electronics are poorly standardized. Before the now-ubiquitous mobile phones and their micro-USB charging ports, the most common type was the cylindrical barrel connector, with the female plug having a ground or negative sleeve and a positive contact on the inside. This mates with a male jack that must not only accept the plug’s outer diameter (OD), but must also have a pin matching the plug’s inner diameter (ID). OD ranges from 2.35 to 6.9 mm, and ID from 0.65 to 4.3 mm. Common sizes are 5.5 mm OD × 2.5 mm ID, 5.5 mm OD × 2.1 mm ID, and 3.5 mm OD × 1.3 mm ID. There are barrel adapters with four-way (X-connector) plugs or six-way (star connector) plugs to fit a variety of sockets.
- The much older jack plug or phone plug/jack for audio signals (see TRS) is sometimes also used for DC power.
- DCE
- (1)
- Data Communications (or Circuit-terminating) Equipment. A transmitter and/or receiver (e.g., a modem) that’s part of a data transmission system. It provides the clock signal for the transmission. Contrast DTE.
- (2)
- Distributed Computing Environment. A flexible client-server architecture for heterogeneous platforms.
- DCG
- Dynamic Cognitive Game. A more advanced form of reverse Turing test than the CAPTCHA, requiring users of an Internet site to solve a quick puzzle that a bot, presumably, can’t.
- DCL
- Digital Command Language. The VMS command set.
- DCMA
- Dynamic Channel Multicarrier Architecture. A technology developed by ComSpace Corp., and used for specialized mobile radio networks that can configure the number and bandwidth of voice and data channels based on a carrier’s requirements.
- DCOM
- Distributed Component Object Model. A Microsoft Windows “standard” for communication between apps on different Windows computers. Introduced with Windows 98 as a DLL and dropped after Windows 2000 Professional, it’s essentially a hasty modification of COM meant to keep out CORBA.
- DCR
- Direct Current Resistance.
- DCS
- Distributed Control System. See SCADA.
- DCT
- Discrete Cosine Transform. A technique common in lossy image compression. See JPEG.
- DDC
- Digital Down-Converter. A unit that converts a signal from RF to baseband without any IF, by using high-speed sampling and A/D conversion.
- DDE
- Dynamic Data Exchange. The 1989 Microsoft predecessor to OLE. It allows applications on the same computer to exchange text and share commands through a device driver called a DDE server. It’s slow, and both apps must be running for it to work.
- DDM
- Direct Digital Manufacturing. Making a physical object directly from a computer design, most often with 3D printing.
- DDNS
- Dynamic Domain Name System. A method that quickly updates DNS information on domains or URLs. It exists because some domains change their data more frequently than the original DNS was designed to accommodate.
- DDoS
- Distributed Denial of Service. Like DoS, a network attack that tries to overwhelm a server. The difference is that it uses a large number of sources to send bogus requests (e.g., SYN or ICMP packets) or junk data, so it’s harder to deal with. A popular way to defend a site against this is to host it on a CDN.
- The standard platform for DDoS is a bot program infiltrating many different computers. Whenever a bot-infected host (a zombie) is connected to the network, its bot secretly establishes a backchannel to some pre-defined control site, where the controller can command all active bots to launch a simultaneous attack using their host resources. Compare DRDoS, and see also malware.
- DDoS services are available for hire on the Internet. To give themselves some thin legal cover, the operators often advertise them as services for stress-testing networks.
- DDP
- Datagram Delivery Protocol.
- DDR#
- Double Data Rate. A family of PC main memory technologies: DDR, DDR2, DDR3, DDR4, DDR5, and DDR6. See DRAM.
- DDS
- Direct Digital Synthesizer (or Synthesis). A device (or process) that generates an analog waveform from digital input. At each clock cycle, a phase accumulator adds some increment Δθ, and the new phase value provides the address for a look-up table (LUT) of waveform samples. A DAC converts the look-up table outputs into the analog signal. Modulation can be added to this process.
- DD-WRT
- A GPL-compliant firmware created to replace manufacturer firmware in wireless routers. It’s popular in open-source circles. DD is the license plate code for Dresden, Germany, where the project began, and WRT is for the Linksys WRT54G series routers for which the firmware was initially written. The project lives on at https://dd-wrt.com/.
- DE
- Directed Energy. In addition to lasers, this refers to narrow-beam HPM weapons intended to disable drones and other small systems by inducing electric fields that scramble or damage their electronics.
- DE-9
- The proper name for the connector popularly called a DB-9. See D-sub.
- dead bug
- Besides being a simple core-strengthening exercise, this refers to a leaded microchip lying upside-down. Dead-bugging is the test & development practice of soldering other circuit contacts to a chip in this position.
- debounce
- Filtering a signal to eliminate spurious fluctuations (bounces) that can occur when an input is changing state. For example, a mechanical switch might rapidly and repeatedly make and break contact while being pressed or toggled, so debouncing its state would prevent a fluctuating system response.
- DEC
- Digital Equipment Corporation. Manufacturer of VAX workstations, Alpha microprocessors, VMS & Ultrix operating systems. Bought in 2000 by Compaq, which was in turn bought in 2002 by Hewlett-Packard (HP) after an ugly public dispute between HP management and shareholders.
- decade
- A 10:1 increase or decrease in a variable, usually frequency. Most often used in describing change in signal gain over a frequency range. For example, if a signal response varies as 1/f, then at f0 it will be some value P, and at 10f0 – a decade higher – P/10. So the response exhibits a 20 log [(P/10)/P] = -20 dB/decade rolloff. An octave is a 2:1 change, so the same 1/f response equates to 20 log [(P/2)/P] = -6.02 dB/octave. See dB.
- declination
- See equatorial system.
- DECnet
- DEC’s VMS-based network protocol.
- DECNIS
- DEC Network Integration Server. A router for DECnet networks.
- DeCSS
- De-Content Scrambling System. CSS is an older encryption system for commercial video DVDs. DeCSS is a software utility published in 1999 that decodes CSS. It has been the object of numerous lawsuits.
- deep learning
- An advanced category of machine learning intended for more complex data, in which the algorithm is able to make iterative changes to itself to improve its performance in classifying input, or predicting outcomes based on input. See artificial neural network (ANN).
- DELNI
- Digital Ethernet Local Network Interconnect. A DEC Ethernet concentrator with an 8-device capacity.
- delta modulation
- Actually a variant of the PCM analog-to-digital technique, not a modulation type. The source is encoded by transmitting the difference between the amplitude of a sample and that of the previous sample.
- DEMS
- Digital Electronic Message Service. A point-to-multipoint microwave network, mostly used by businesses as a broadband MAN. It was originally in the 18 GHz band, but was moved to the 24.25-24.45 GHz and 25.05-25.25 GHz bands to make room for military satellite comms.
- DEP
- Data Execution Prevention. An OS security feature originated by Microsoft and now available for most systems. It designates regions of memory as non-executable to prevent malware buffer-overrun exploits. Microsoft DEP might be disabled by default for non-Microsoft programs because of the likelihood of false alarms. See also ASLR.
- Intel and AMD processors from 2005 on have hardware DEP, which they respectively call Execute Disable (XD) and No-Execute (NX). These features are distinct from the later so-called Trusted Computing initiative, although the latter might make use of them.
- derivative
- One of the fundaments of calculus. Given some variable x, and some function y = f(x), meaning its value is dependent on x, the derivative of y with respect to x is the rate at which the value of y changes relative to the value of x. For example, if x is time (in seconds), and y is a formula for distance (in meters) with respect to time, then the first derivative of y with respect to x is speed (in meters/second).
- The first derivative of a function y with respect to x is commonly denoted as dy/dx, or sometimes as y'. Higher-order derivatives exist, although they might not be meaningful, depending on the function. For example, the second derivative y'' or d2y/dx2 of position with respect to time (which is the first derivative of speed with respect to time) is acceleration, in meters/second2. [A 2019 study showed that a better representation of a second derivative is d2y/dx2 - (dy/dx)(d2x/dx2).]
- The derivative of a constant is always zero. Hence, if distance is not changing with respect to time, then its first derivative – speed – is zero. Similarly, if speed is constant, then the second derivative of distance with respect to time – acceleration – is zero.
- The process of calculating a derivative is differentiation. The inverse of a derivative is an integral.
- DES
- Data Encryption Standard. See encryption.
- device driver
- Software that allows a computer to use a specific piece of installed or externally connected hardware. The OS routes all tasks requiring the device to its driver, which communicates with the device via the system data bus the device is connected to. In MS-DOS, the command ‘DEVICE =’ implements a driver.
- Operating systems have many common or standard drivers pre-installed. If that doesn’t suffice, the hardware manufacturer will typically make the necessary driver(s) available for download online, often as part of some larger app for managing the device. The practice of providing a copy on some physical medium (thumb drive, DVD, CD, floppy) is in decline as of 2025. See VxD, BSP.
- DevOps
- Development Operations. See process management.
- DevSecOps
- Development Security Operations. See process management.
- DEW
- Distant Early Warning. The DEW Line was a network of radar stations established by the US & Canada starting in the early 1950s to watch for Soviet bombers coming over the Arctic or northern Pacific Ocean, with human operators passing data by phone to SAGE sites. It stood down in 1993.
- dew point
- The temperature, for a given atmospheric pressure and humidity, at which rates of water condensation and evaporation will be equal and, by definition, relative humidity (RH) will be 100%. It can’t exceed actual temperature. If temperature falls to the dew point and continues falling, dew point declines with it, usually producing fog and condensation. Rising humidity raises the dew point, while rising pressure lowers it, so high-pressure weather systems initially bring drier, clearer conditions. See RH.
- DF
- Direction-Finding.
- DFA
- Doped Fiber Amplifier. See EDFA.
- DFB
- Distributed Feedback. A semiconductor laser that incorporates a diffraction grating into the chip, typically along the length of the lasing cavity. The grating reflects a single wavelength back into the cavity, forcing a single resonant mode and producing a stable, narrow-band output.
- DFN
- Dual Flat Non-leaded. See JEDEC.
- DFP
- Digital Flat Panel. See graphics.
- DFT
- Discrete Fourier Transform. See Fourier transform.
- DFTS
- Discrete Fourier Transform Spread.
- DGPS
- Differential GPS. A ground-based add-on to GPS. It requires a network of GPS receiver stations that transmit a correction signal. Any DGPS-enabled receiver in the covered area can use the signal to improve position accuracy to within 3-5m. The U.S. Coast Guard operates the most widely used DGPS service.
- DHCP
- Dynamic Host Configuration Protocol. A member of the TCP/IP protocol suite at the Application layer, based on Bootp. When a device joins or logs on to a DHCP-supporting network, it uses DHCP to acquire an IP address and other network parameters such as the DNS server address from the router or server. This makes it easy for new devices to join. For security purposes, some versions of DHCP permit the network administrator to define a whitelist of MAC (hardware) addresses, and block access from addresses not on the list.
- DHFC
- Direct Hydrogen Fuel Cell. See fuel cell.
- diac
- From “diode AC”. See thyristor.
- dictionary attack
- Whereas a brute-force attack on account security tries every possible combination, the dictionary attack is a malware password-guessing technique in which a long list of possible passwords, both common and uncommon, is tried on targets. Despite the name, these lists are not restricted to dictionary words such as
password. They include common variations of capitalization, character/letter substitution, and word-number combination such asp@ssw0rdorPa$$word1, and also frequently used strings of numbers, letters, and/or words:12345,54321,abcde,LetMeIn,MyAccount,myfacebookaccount,OpenSesame, common names, etc. - An obvious defense is to disallow repeated, short-interval login attempts, so that the attacker gets only a few tries. However, too strict a policy creates another vulnerability, to DoS attack: a few bogus login attempts can lock out valid users.
- die
- In electronics, this means a piece of semiconductor material with an integrated circuit laid out on it. The standard fabrication process starts with a purified, polished semiconductor wafer, uses photolithography to etch multiple copies of a circuit into the wafer, and then cuts up the wafer (a process called singulation) to create a batch of identical dies. This process is longer and more complex than it sounds. A completed die still needs to be packaged for use.
- dielectric
- Any insulating material that becomes electrically polarized in response to an applied electric field, but still without conducting current. Air is a dielectric.
- differential encoding
- Re-coding a NRZ-L binary sequence so that each differentially encoded bit is the modulo-2 (XOR) sum of the previous differentially encoded bit and the current message bit. The encoded NRZ-M or NRZ-S data stream therefore reflects changes in the original message stream rather than values relative to a fixed standard, so that the transmitted symbol changes at every tick of the baud clock. This reduces detection error at the receiver, and is almost universal in modems. It must be done after any bit interleaving, however.
- Differentially encoded transmissions are usually, but not always, received using differentially coherent detection. This is called DPSK.
- digital certificate
- A data packet provided by a trusted certification authority (CA) to authenticate the source of some digital object – Web site, e-mail, document, software program, etc. – to users of that object. In some cases, it also provides a cryptographic hash to verify that the object has not been modified since the source released it. Digital certificates typically have expiration dates, and can be revoked by the CA before the expiration date, although users can still choose to accept expired or even revoked certificates.
- This scheme usually relies on a public-key infrastructure. It vouches for the source, but does not ensure that the object is safe, or that it really is what the source claims it is.
- At the base of the PKI approach is the CA’s self-signed root certificate. Its private key is used to sign other certificates issued by the CA. Modern operating systems and some applications come with a set of root certificates that they use to validate both Web sites and applications.
- digital lock
- This refers to two different things: 1) a hardware lock that’s opened by some sort of digital input rather than a physical key, and 2) password-protected software controls added to a file or other digital medium to restrict user ability to view or copy it, or to change its location in a file system. The second meaning is also called a technological protection measure (TPM).
- digital twin
- A computer model that accurately simulates a physical device or system, for use in analysis and testing.
- DIMM
- Dual In-line Memory Module. A circuit card holding DRAM (PC main memory), with some number of flat contacts in two equal sets on opposite sides of the module’s bottom edge. Unlike those of the older SIMM, contacts on opposite sides are separate and unconnected. Consumer DIMMs are mostly unbuffered, i.e., no buffer between memory and the memory controller/processor, and lack error-checking & correction (ECC). This makes them cheaper and slightly faster than DIMMs that do have these features. Some variants of the basic DIMM, for special applications requiring higher reliability or greater capacity, or both:
- CDIMM – Clocked DIMM. Uncommon term, probably means the same thing as either RDIMM or CUDIMM.
- CSODIMM – Clocked Small Outline DIMM. A SO-DIMM with the same clock driver signal described for the CUDIMM.
- CUDIMM – Clocked Unbuffered DIMM. (2024) These add a clock driver (CKD) signal for maintaining stability at high signaling frequencies.
- FB-DIMM – Fully Buffered DIMM.
- RDIMM – Registered DIMM. Has a buffer, aka a register, beween the memory and the memory controller to stabilize and improve memory management. Usually also has ECC.
- SO-DIMM – Small Outline DIMM. For laptops and other space-constrained devices. See SO-DIMM.
- UDIMM – Unbuffered DIMM. Usually means it has ECC for improved reliability. Sometimes, confusingly, it means plain old DIMM.
- Standard DIMM sizes:
- 100-contact – 3.5" × 1.25". Used in printers and other devices, not in PCs.
- 200-contact – Uncommon. Used in printers and other devices, not in PCs.
- 168-contact – For FPM DRAM, EDO DRAM, and SDRAM (PC66, PC100, & PC133) in 64-bit Pentium and AMD Athlon PCs. It’s 5.25" long × 1.5" to 1.7" high, and the bottom edge has two notches that divide the contacts into groups of 20, 60, and 88. Smaller rack spaces led to the compatible 168-pin LP (low profile) DIMM, which is less than 1.2" high.
- 184-contact – For 64-bit SDRAM (PC2100, PC2700, PC3200, & PC3500) or DDR SDRAM on Pentium III, Pentium 4, and AMD Athlon PCs. Measuring 5.25" long × 1.375" high (about – height varies), it was the dominant DRAM form factor in 2003. A notch on the bottom edge divides its contacts into groups of 80 and 104. The compatible 184-contact LP (low profile) and 184-contact VLP (very low profile) DIMMs are less than 1.2" and .72" high respectively.
- 240-contact – For 64-bit DDR2 and DDR3 SDRAM. 5.25" long, and usually LP (under 1.2") or VLP (under .72"). The notch in the bottom edge divides its contacts into groups of 112 and 128 (DDR2) or 96 and 144 (DDR3), so DDR2 DIMMs can’t be forced into DDR3 slots and vice versa.
- 288-contact – (2014) For 64-bit DDR4 SDRAM, the notch divides its contacts into groups of 154 and 134. (2020) For 64-bit DDR5 SDRAM, the notch is shifted slightly to make it physically incompatible with DDR4-only slots, dividing its contacts into groups of 150 and 138.
- DIN
- Deutsches Institut für Normung (German Standards Institute). In the US, this term commonly refers to one of three things based on DIN standards:
- (1)
- The DIN rail, a 35mm wide steel rail for mounting equipment in laboratory equipment racks.
- (2)
- The width × height of vehicle in-dashboard stereo units, adopted as ISO standard 7736. A single DIN panel slot is 180 × 50 mm, and a double DIN is 180 × 100 mm. Depth is not specified.
- (3)
- The DIN and mini-DIN connectors used for keyboards, mouses, and various other devices. There are many proprietary uses of these connectors, so the pin numbering, position, and signal allocation might vary. Standards exist for 5-, 7-, and 8-pin DIN and 3- through 9-pin mini-DIN. IBM used the 5-pin DIN for the keyboard on its PC-XT and PC-AT, and the 6-pin mini-DIN on its PS/2 series, for which reason the 6-pin is commonly called a PS/2 interface. PS/2 keyboards exist with both types, but mouses are not made with full-sized DIN connectors.
- DIN 5 and mini-DIN 6 are electrically compatible, so an adapter will change one to the other. Beware, however: Some of the newer bus mice still use a mini-DIN form factor, but are not compatible with PS/2 ports. For the DIN 5, pin 1 = clock, pin 2 = data, pin 4 = GND, and pin 5 = +5V. For the mini-DIN 6, pin 1 = data, pin 3 = GND, pin 4 = +5V, and pin 5 = clock. The Intel/Microsoft PC System Design Guide specifies green for mini-DIN mouse ports and purple for keyboard ports.
- diode
- From the Greek for “two path”. A one-way gate for electric current. Solid-state crystal diodes were developed at the beginning of the 20th century, but the vacuum-tube diode (a two-terminal thermionic valve) invented in the 1920s was for many years more useful. Reliable, precise solid-state technologies began to replace vacuum tubes in the 1950s.
- In its most basic form, the modern diode is a pn junction: a semiconductor with a positively doped and a negatively doped terminal. Where the two materials touch, a depletion region forms – a thin layer almost emptied of both negative and positive charge carriers (electrons and holes), so that it acts as an electrical insulator.
- Applying a positive voltage to the anode p, a condition called forward bias, shrinks the depletion region. If bias voltage reaches some modest threshold (typically 0.7 V) set by the diode’s construction, the depletion region vanishes, and current flows readily from p to n. The diode is not a linear device, so it doesn’t follow Ohm’s Law – that is, bias voltage v1 produces current i1, and v2 produces i2, but (v1+v2) doesn’t produce (i1+i2). Large increases in forward-bias current cause little increase in voltage, so many system designs treat voltage drop across a forward-biased diode as a constant.
- Reverse bias – applying a positive voltage to the cathode n – expands the depletion region and increases its already high resistance (again, in a non-linear fashion), so the diode effectively blocks reverse-bias current. Increasing reverse-bias voltage until avalanche breakdown occurs forces a current through, but if the diode is not designed to tolerate this condition, it will be destroyed.
- Commercial diodes usually have a stripe on the cathode to show the proper orientation. Special classes of diode:
- avalanche photo-diode (APD) – A type of PIN or PN photo-diode that operates at a high reverse-bias voltage. It undergoes non-destructive avalanche breakdown in response to incident light, and is very sensitive – potentially capable of single-photon detection.
- LED (light-emitting diode) – A diode that emits light when forward-biased. It’s typically in series with a resistor to limit current and prevent overheating. Functionally, it can be viewed as the inverse of the photo-diode. The first ones were red, but they’re now made in all colors. There are even LEDs that operate at wavelengths outside the visible range, as far out as the harmful UV-C rays. The bandgap (electron-hole recombination) energy of the semiconductor determines emitted wavelength.
- MIM (metal-insulator-metal) diode – Permits one-way electron quantum tunneling across a thin insulating barrier, and therefore handles extremely high (optical) frequencies. Researchers (2010) predict it will replace the silicon and transistors ubiquitous in electronics, making them faster and cheaper.
- photo-diode – A diode that, in reverse-bias state, breaks down in response to incident light above a certain intensity. Used as a photo-detector.
- PIN (positive-intrinsic-negative) diode – A diode with an undoped (intrinsic) region between the customary p and n regions. It will pass a high-frequency signal without going into reverse bias.
- Schottky diode – Also Schottky barrier diode, named for German scientist Walter Schottky. A metal-to-silicon (n or p) junction diode. Compared to the conventional pn junction, it has a smaller forward bias voltage (typically 0.15-0.45V) and much smaller capacitance, permitting much faster electron-hole recombination and hence much faster switching times. This makes it especially useful in rectifiers.
- tunnel diode – A narrow, heavily doped pn junction passes a quantum tunneling current at low forward bias. The current drops (!) with rising bias voltage, exhibiting negative resistance, then shoots up again at high forward bias. It can operate at very high frequencies, far into the microwave band, but is little used.
- Zener diode – Named for Bell Laboratories physicist Clarence Zener. Exhibits reverse-bias avalanche breakdown at a specific voltage without being destroyed, so it can function as a voltage regulator.
- DIP
- Dual In-line Package. See JEDEC.
- dipole
- See antenna.
- Direct Rambus
- Proprietary CPU-RAM bus technology from Intel and Rambus, Inc. With 400 MHz DRAM, it yields a memory bandwidth of 1.6 GB/s. See DRAM.
- DirectX
- Microsoft’s collection of APIs for multimedia applications, giving Windows programmers relatively quick access to system hardware. DirectX 11 is the newest version as of mid-2012. Most computer industry references to DirectX are really talking about Direct3D, DirectX’s API for 3D video graphics.
- dirtbox
- From Digital Receiver Technology (DRT), Inc., the Boeing subsidiary company that developed it. A mobile-phone cell tower simulator (a.k.a. IMSI catcher) operated by someone other than the mobile wireless provider. As a law enforcement tool, it acts as the connecting tower for mobile phones within range, and can record communications and track suspects. It’s similar to the better-known stingray, but with greater range because it’s intended for airborne use.
- disassembler
- See assembler.
- disc or disk
- Apple weighed in early and hard with the position that “disk” refers to a magnetic storage medium, and “disc” to an optical medium. Other views persist. In American English, a cylinder with height much less than its diameter is indisputably a disk, but there is room to dispute the height:diameter ratio below which this change of nomenclature occurs.
- DisplayPort
- See graphics.
- distribution frame
- An equipment rack, or set of racks, that connects users and/or other distribution equipment to network services using some combination of cables and wireless links. Specific types:
- BDF – Building Distribution Frame. Provides the network interface for a building. It can functionally act as a IDF or MDF, or a combination of the two.
- CDF – Combined Distribution Frame. Fills the role of both MDF and IDF, i.e., it interconnects IDFs but also provides connections for individual users.
- IDF – Intermediate Distribution Frame. A subordinate node of a MDF, serving as an access point for individual users or an interconnect for other distribution frames.
- MDF – Main Distribution Frame. The termination point for external trunk cables from the larger network, it provides interconnection for subordinate IDFs or BDFs, or, in smaller systems, connects the users directly.
- ODF – Optical Distribution Frame. A distribution frame that uses fiber-optic cable.
- divestiture
- The government-mandated 1984 breakup of AT&T. The FCC established 164 local access and transport areas (LATAs) throughout the US, each one corresponding to an area code, more or less. It defined two types of service providers: local exchange carrier (LEC) and inter-exchange carrier (IXC). A LEC could provide service only within a single LATA, and an IXC only between LATAs.
- AT&T therefore divested itself of 22 local Bell Operating Companies (BOCs), which, as LECs, were prohibited from manufacturing equipment, having any relationship with AT&T, or discriminating for or against any particular IXC. Each BOC was confined to a single state.
- To own and manage the 22 BOCs, seven Regional Bell Holding Companies (RBHCs) of roughly equal size were created. These were the so-called “Seven Dwarfs”, or “baby Bells”: Ameritech, Bell Atlantic, BellSouth, NYNEX, Pacific Telesis, Southwestern Bell, and US West. Each was confined to one region of the US. AT&T was left with the long-distance business, equipment manufacturing, and the part of its R&D department (Bell Labs) that it later spun off as Lucent. The rest of Bell Labs became Bellcore, jointly owned & managed by the seven RBHCs.
- As of March 2003, thanks to mergers, four RBHCs remain: Verizon (includes Bell Atlantic & Nynex), SBC (includes Southwestern Bell, Pacific Telesis, & Ameritech), BellSouth, and Qwest (includes US West). They act as holding companies for BOCs and unregulated subsidiaries within their areas.
- DKE
- Dunning-Kruger Effect. Named for a 1999 study by psychiatric researcher David Dunning and his student Justin Kruger, this is the tendency of people to overestimate their own abilities in proportion to their observed degree of ignorance or incompetence. Per Dunning & Kruger, the effect occurs because the deficits that lead to ignorance and incompetence also inhibit, in similar degree, the ability to recognize them.
- DKIM
- DomainKeys Identified Mail. See e-mail authentication.
- DLC
- (1)
- Distributed Loop Carrier.
- (2)
- Downloadable Content. Video gaming term for additional features, capabilities, in-game items, etc., available for Internet download separate from the game itself, usually for a price.
- DLCC
- Dual Leadless Chip Carrier. See JEDEC.
- DLL
- (1)
- Dynamic Link Library. An executable Windows (or OS/2) binary that contains specialized data, functions, and other resources; referred to under .NET as a class library. Applications can use these resources by establishing either a static (remains while program runs) or dynamic (re-established as needed) link to the DLL that offers them. Besides the familiar .dll, DLL files can have .exe, .drv, or .fon extensions.
- DLLs do everything COM objects can, and are quicker and easier to make. This is a mixed blessing, since everyone and his brother does modify them or make their own, and if a linked app can’t find the DLL it expects, it won’t run correctly. Consequently, many stand-alone apps still use the old static library approach (RTL), which compiles the needed library functions into the executable.
- (2)
- Delay Lock Loop. A logic function to eliminate delay between the clock inputs to the different components of a device.
- DMA
- Direct Memory Access. In a PC, the technology that transfers data from main memory (DRAM) to a peripheral or external device without passing it through the CPU. This greatly eases the burden on the CPU, and is standard in the memory controllers of modern motherboards. It also leaves a nearly undetectable way for devices with embedded malware to take over the system, although this sort of hardware-based attack has not yet (2013) been seen outside of research labs.
- First party DMA (also called bus mastering), used by PCI devices, allows the peripheral device initiating the transfer to take over the system bus and act as controller on its own behalf. Standard (or third-party) DMA, as implemented by the now-obsolete ISA bus, requires that the system DMA controller perform the transfer between the sending and receiving devices, which slows the transfer down.
- Another kind of DMA called programmed I/O (PIO) is used in hard drives conforming to the later ATA standards.
- DMARC
- Domain-based Message Authentication, Reporting, and Conformance. See e-mail authentication.
- DMC
- Discrete Memoryless Channel. A model of a transmission channel with no memory and a finite (discrete) set of inputs and outputs. The BSC is one example.
- DMCA
- Digital Millennium Copyright Act. Much-hated 1998 anti-copying law that, in light of legislation that came later, looks almost genteel.
- DMD
- Differential Mode Delay. The difference in propagation rates between modes in multi-mode fiber.
- DMFC
- Direct Methanol Fuel Cell. See fuel cell.
- DMI
- Desktop Management Interface. A standard that calls for a service layer (ideally part of the OS) to be present on every PC. It would collect information about the PC, its peripherals, and its software, and make this available to management applications (e.g. a network) via a standard interface.
- DML
- Direct Modulated Laser.
- DMM
- Digital Multi-Meter. A meter, typically handheld, with the capability to measure electrical resistance, AC or DC voltage, and AC or DC current. Unlike an analog meter, it doesn’t apply a 9V level to measure resistance, making it safer for modern electronics.
- If a device under test (DUT) has low resistance, a conventional 2-wire DMM won’t get an accurate reading because of the added resistance in the leads connecting DMM to DUT. A 4-wire DMM, which is typically not a handheld device, uses a separate pair of leads to measure voltage across the DUT, and uses that data to correct for the lead resistance.
- DMT
- Discrete Multi-Tone. An ANSI standard modulation technology for ADSL that breaks the twisted pair bandwidth from about 10 kHz to 1.1 MHz into 256 independent channels, each just over 4 kHz. Each of the subchannels is dynamically quality-tested and assigned a QAM bit rate, which can be changed if subchannel quality changes. (This technology is also referred to as OFDM with discrete Fourier transform modulation/demodulation.) The first six channels are reserved for voice. Upstream data uses up to 24 channels. Downstream data uses 248 channels if echo cancellation is used, 222 if it’s not. This technology is generally superior to CAPM.
- DNA
- Deoxyribonucleic Acid. The molecular code for all known life, encoded with the base pairs adenine/thymine and cytosine/guanine (A/T and C/G). Researchers are pursuing the use of synthetic DNA as an extremely dense storage medium for digital data. The technology for writing it is the hard part, but see CRISPR.
- DNI
- Do Not Install. Also called DNP. A direction in schematics indicating that a component should not actually be installed in the finished circuit. The footprint is there to allow a part to be placed later, for testing or other purposes.
- DNN
- Deep Neural Network. Same thing as ANN.
- DNP
- Do Not Populate. Same as DNI.
- DNP3
- Distributed Network Protocol. A set of communications protocols used by many of the SCADA networks monitoring and controlling the US electric grid.
- DNS
- Domain Name System. The system that maps Internet URLs to global four-byte IP and 6-byte IPv6 addresses, in effect acting as a phone book for the Internet. This is what allows users to contact and access Internet sites using names rather than numerical addresses (although browsers accept either). A DNS server is a host that provides this name-to-address translation. Most ISPs and corporate networks have their own. Modern operating systems and routers cache DNS addresses to save time. To get around censorship or domain blocking by an ISP’s or network’s DNS service, users can manually configure their operating system to use a different DNS server, but this can also increase their system’s vulnerability to malware.
- DNS traffic normally goes through TCP/UDP port 53. It can be encrypted with TLS; or with HTTPS, the secure version of HTTP, using dedicated port 853.
- ICANN still (2016) manages the DNS under contract from the US Department of Commerce’s National Telecommunications and Information Administration (NTIA), but NTIA has declared its intent to give up formal stewardship in the near future. The DNS rests on a hierarchy of 13 logical root servers. At the top is the A root name server based in Herndon, VA, which VeriSign (formerly NSI) runs under contract with ICANN. Every 12 hours, it generates the root zone file, a ~200 kB listing that tells the other 12 servers (B through M) which Internet domains exist and the IP addresses of the servers responsible for them. Only three root servers – I, K, and M – were outside the US in the late 1990s, but now most of them are effectively international, since each logical server has become an array of redundant physical servers with wide geographical distribution.
- One rung below the root name servers are the servers that house Internet top-level domains (TLDs). Up through the early 2000s, this was a slowly changing list of more than 200 country-code top-level domains (ccTLDs), and a much smaller number of US-based generic top-level domains (gTLDs) including .com, .edu, .gov, .mil, .net, .org, .int, .biz, .info, .aero, .coop, .museum, .name, and .pro. In 2011, ICANN began allowing the registration of customized gTLDs, and the number expanded to the low thousands.
- The ccTLD for the USA is “.us”. Some others:
- Some national registrars implement their own versions of gTLDs. For example, Mexico uses the .com.mx sub-domain for commerce sites, while the UK has .co.uk for that role.
- A DNS sinkhole is a server that intentionally redirects DNS requests to non-existent addresses, blocking access to the domains it’s supposed to handle. It’s used to stop botnet traffic, and for cultural or political censorship. Some operating systems have a hosts file that can be modified to block traffic from domains known to be a problem.
- DNSSEC
- Domain Name System Security Extensions. Just what it says: a security add-on for the DNS, which wasn’t designed for the security threats that have since emerged. It mandates digital signatures for DNS lookup data, to prevent search redirects and cache poisoning of DNS queries.
- DOCSIS
- Data-Over-Cable Service Interface Specification. An ITU-approved standard for two-way data communication over a HFC cable TV network using cable modems at the subscriber end. Version 1.0 (1997) has upstream (from the subscriber) rates of 320 kb/s to 10 Mb/s in the 5-42 MHz band, and downstream (to the subscriber) 27-36 Mb/s rates in the 50-750 MHz range. Version 3.1 (2013), using 4096-QAM with OFDM sub-carriers, has downstream rates up to 10 Gb/s and upstream rates up to 1 Gb/s. Data rates actually available to subscribers are much lower, and drop further as the number of subscribers rises. Each version is backward-compatible with previous versions. There is also a EuroDOCSIS.
- DOM
- Document Object Model. A W3C standard API for presenting a HTML, XHTML, or XML document as an object so that programs or scripts can modify it.
- dongle
- Origin unknown (“Don Gall” is a myth that originated in a 1992 ad campaign) but undoubtedly derived from “dangle”. Originally, a hardware key for a software license. It plugs into a PC data port – serial, parallel, RJ45, HDMI, USB, etc. The meaning of the term has broadened with time to include any such plug-in device with a function beyond simple data storage, such as a wireless transceiver, or a pigtail that connects a PC card or circuit-card interface to an Ethernet jack.
- DoS
- Denial of Service. A brute-force network attack to shut down a server by barraging it with bogus data or requests, either to overload its processing resources or to clog its bandwidth. As defenses have improved, more sophisticated attacks such as DDoS and DRDoS have emerged.
- DOS
- Disk Operating System. Any of the old single-tasking, command-line interface (CLI) operating systems that ran PCs from the 1970s well into the 1990s, before giving way to GUI systems such as MS Windows and Mac OS. This excludes CLI multi-tasking operating systems such as Unix. Some single-tasking applications, such as embedded devices or industrial control systems, still use DOS.
- For its original 1981 PC model 5150, IBM used PC-DOS, its own proprietary tweak of Microsoft MS-DOS 1.0. However, the PC could also run the cheaper MS-DOS, the opening that led to Microsoft’s eventual dominance in the PC market. Other contemporary rivals included Digital Research DR-DOS and CP/M. FreeDOS, a 1994 GPL release that’s still being maintained and upgraded, is backward-compatible with MS-DOS applications and is accessible at https://www.freedos.org.
- Main memory (DRAM) under MS-DOS consists of the following sections:
- conventional memory – The first 640 kB, for use by applications. Its addresses, in hexadecimal format, are 0x00000 to 0x9FFFF.
- upper (reserved) memory – The 384 kB above conventional memory. Its presence is the cause of the old 640 kB memory barrier in the first IBM PCs and subsequent clones. It has 128 kB reserved for use by the video adapter card; 128 kB for the BIOS from any adapter board ROM, including the video adapter (e.g. VGA’s BIOS uses 32 kB here), hard drive controller, etc.; and 128 kB for system BIOS, POST, and bootstrap loader. Not all of this reserved space is necessarily used. The DOS commands LOADHIGH (LH) and DEVICEHIGH tell the called program to use upper memory blocks (UMBs) seized for use as conventional memory, if there are any.
- high memory area (HMA) – The first 64 kB (minus 16 bytes) of extended memory above upper memory. Device drivers that normally require conventional memory can be loaded here. DOS=HIGH in the CONFIG.SYS loads the DOS kernel here, freeing 40 kB of conventional memory.
- extended memory – Any memory beyond the first 1024 kB (1 MB), including HMA. PC-XT systems can have only 1 MB of memory, and so can’t use extended memory.
- DOS has a scripting method known as a batch file, based on the Unix OS’s more powerful shell script. A batch file is a series of DOS and/or system commands stored in a plaintext file, usually with a .bat filename extension. Entering the file name in MS-DOS runs the commands from the file in order. MS-DOS systems have a batch file named
autoexec.batrun at startup by a call from thecommand.comsystem file. - Versions of MS Windows from Windows NT onward don’t use MS-DOS. That’s why their command prompts, although they look like DOS windows, don’t recognize most DOS commands. They can still run batch files that use the commands they do recognize.
- dot-com
- From .com, the most popular top-level domain (TLD) for US commercial Internet servers. A dated term for a business that operates mostly or entirely on the Internet. It fell out of use as that became the norm.
- dot product
- A mathematical operation used in analyzing the behavior of EM fields, among other things. Also called vector product or inner product. Given two vectors x and y, the dot product [x • y] is the product of the vector magnitudes and the cosine of the angle between them: |x| |y| cos θ. It’s a scalar, not a vector. If the vectors are represented as equal-length arrays, e.g. [x1 x2 x3] and [y1 y2 y3], the dot product is calculated as [x1 × y1] + [x2 × y2] + [x3 × y3]. Compare with cross product.
- DOV
- Data Over Voice. A technology that transmits data and voice simultaneously over a twisted-pair line. Typical data rates are 9.6 or 19.2 kb/s.
- doxing
- See troll.
- DP
- See DisplayPort.
- DPBX
- Digital Private Branch Exchange. See PBX.
- DPDT
- Double Pole, Double Throw. See switch.
- DPI
- (1)
- Dots Per Inch. The number of ink or toner dots a printer uses to make a 1" line. It’s not meaningful for describing screen or scanner resolution, or image size, but is often used for that anyway.
- (2)
- Deep Packet Inspection. Examination of network packet payloads by network nodes that aren’t the addressee. Useful for security and network management, but also for spying and censorship. Avoiding it requires an encrypted connection, whether through Web sites that support TLS and SSL, or a blanket solution such as a VPN.
- (3)
- Direct Power Injection. A type of ESD testing that applies power spikes to transmission lines.
- DPP
- Distributed Parallel Processing. A Novell idea.
- DPRAM
- Dual-Ported Random Access Memory. See MPRAM.
- DPSK
- Differential Phase Shift Keying. If source data undergoes differential encoding prior to PSK modulation, this is sometimes but not always referred to as DPSK modulation. A DPSK receiver uses differentially coherent detection (comparing the signal to a one-symbol-delayed version of itself) to simultaneously resolve the transmitted phase shifts and remove the differential encoding. It’s less complex than a standard coherent-detection receiver, but has higher BER due to its greater noise susceptibility. DPSK signals and systems can be more explicitly designated D-BPSK (binary, or 2-state) or D-QPSK (quadrature, 4-state).
- DPST
- Double Pole, Single Throw. See switch.
- D-QPSK
- Differential Quadrature Phase Shift Keying. Identical to QPSK, except for differentially coherent detection at the receiver (which mandates differential source encoding). See DPSK.
- DRAM
- Dynamic Random Access Memory. Volatile RAM used for main memory in computers, and sometimes as video RAM (VRAM) on graphics cards. Traditionally, it stores data by charging, or not, a capacitor in each memory cell. Since the charge continually leaks away, it requires constant refreshes to maintain state, making it power-hungry and relatively slow compared to the processor clock. Offsetting these disadvantages, DRAM is cheaper and takes less space than SRAM. Memory must be at least as fast as the motherboard, so new types of DRAM are constantly developed as CPUs, chipsets, and peripherals get faster, and it’s all a bit confusing.
- Memory types with 64-bit buses, standard since the late 1990s, come in variants: registered (a register chip delays data 1 clock cycle to make sure synchronization is perfect), buffered (regenerates signals to prevent electrical decay in large memories), or unbuffered with ECC (error checking & correction, requiring 72 rather than 64 bits). Registered or buffered types normally have ECC as well and are for servers and high-end machines, as they boost reliability but decrease speed.
- The throughput of older memory technologies is simply width × clock rate of their front side bus (FSB, also called system bus). Since the introduction of DDR, it’s no longer so simple; DRAM now carries a PC #### rating that gives its throughput in megabytes/second (MB/s). A PC2 ####, PC3 ####, or PC4 #### rating means DDR2, DDR3, or DDR4, respectively.
- Modern motherboards use installed memory at either the rated clock speed of the memory module or the maximum speed of the motherboard slot, whichever is slower. If a motherboard is going to have more than one memory module, best practice is to use modules of the same type, capacity, and clock speed, and ideally the same manufacturer & model number. This avoids any incompatibility issues. Modules of the same type with different speed ratings can usually be made to work together, at the speed of the slower module. Modules of different capacities might cooperate, or not.
- Modern motherboards also support dual-channel memory, meaning their memory controllers can use two 64-bit paths to DRAM as a single 128-bit path. This requires memory modules installed in pairs. Some high-end systems have triple- or quad-channel memory architecture.
- DRAM stores data as multiple banks, each with a two-dimensional memory map addressed by row and column. When the memory controller requests data, it must first precharge and then activate (ACT) the correct memory bank, then select the row with a RAS (row address strobe), and finally access the data with a CAS (column address strobe) read/write. Subsequent access to the same bank skips the precharge and ACT; subsequent access to the same row skips the RAS too.
- DRAM vendors commonly give the memory latency of their products as either a single number (CAS latency) or four timing numbers: CAS latency, RAS-to-CAS delay, RAS precharge, and ACT-to-precharge delay. These are the times, in either nanoseconds or memory bus clock cycles, that each of those four actions takes to complete. Lower is better. ACT-to-precharge is the latency associated with switching to a new memory bank, which is why it’s almost as much as the other three values combined. The memory manager will pipeline memory access so that it starts precharge and ACT on the next bank before it finishes reading the current bank.
- Measured in clock cycles, as they typically are, latency numbers inevitably increase with memory clock speed because each clock cycle gets shorter. This doesn’t negate the advantage of a faster clock, but the relative importance of latency vs. clock speed to overall performance remains a topic of debate. It matters much less than it did because fast, effective L1 and L2 CPU caches have become standard.
- Memory for PC-XT and some PC-AT computers was on DIP IC chips, soldered into place like everything else, sometimes on a motherboard expansion card. These chips varied in capacity (16 to 1024 kB of RAM) and pin count. With the 286 generation of PCs, manufacturers began mounting memory chips on fragile, 30-pin SIPP modules so that users could easily install and remove them.
- Some later DRAM technologies, in roughly chronological rather than alphabetical order:
- FPM DRAM – Fast Page Mode DRAM. Introduced 1987, still common in 1997. Supplied on 32-bit, 72-pin SIMM or 64-bit, 168-pin DIMM, it runs at 25 to 33 MHz clock speed with access times of 80, 70, or maybe 60 ns. Memories with different access times don’t mix.
- EDO DRAM – Extended Data Out DRAM. Introduced 1995, standard by 1997, not much used after the earlier Pentiums, although popular on video cards for a while. It’s typically on 32-bit, 72-pin SIMM or 64-bit, 168-pin DIMM, with 33 to 66 MHz clock speed and 50 or 60 ns access times.
- SDRAM – Synchronous DRAM. Introduced 1996, standard by 2001, outdated but still in wide use by 2006. 64-bit, 3.3V. It synchronizes with the system bus clock at 66, 100, or 133 MHz, and has access times of 8 to 12 ns. It offers only a slight edge over 64-bit EDO DRAM at 66 MHz, much more at 100+ MHz. If system SDRAM is too slow to keep up with the bus, it makes the system unstable. It comes on 168-pin DIMM, 144-pin SO-DIMM, and 144-pin micro-DIMM. Modules are labeled CL2 or CL3 (sometimes CAS2 or CAS3) meaning CAS latency of 2 or 3 clock cycles. CL2 performs slightly better.
- EDRAM – Enhanced DRAM. Also called Cached DRAM. Failed rival to SDRAM.
- DRDRAM – Direct Rambus DRAM, aka just RDRAM. A 1999 proprietary RAM standard that requires a CPU built to work with it. This made it pricey and unpopular, despite the speed advantage that initially won it a spot on Pentium 4 motherboards. The 16-bit RDRAM uses a 266 to 600 MHz bus (PC-600 to PC-1200) and 184-pin RIMM modules that must be installed in pairs. The later dual-channel RDRAM doubles the bus to 32 bits, and has up to 800 MHz clock. Some of the 32-bit types use 232-pin RIMMs. See Rambus.
- SLDRAM – SyncLink DRAM. Unsuccessful would-be successor to SDRAM.
- DDR SDRAM – Double Data Rate Synchronous DRAM. Introduced in 2000 and dominant until replaced by DDR2, this JEDEC open standard does a read/write cycle on both edges of the system bus clock pulse, which doubles its data throughput. With its 64-bit bus, it moves 16 bytes of data per clock cycle, at speeds from 100 MHz (DDR-200, or PC 1600) to 500 MHz (DDR-1000, or PC 4000). It’s deployed at 2.5 V on 184-pin DIMM, 144- or 200-pin SO-DIMM, 244-pin mini-DIMM, and 172-pin micro-DIMM.
- QDR SDRAM – Quad Data Rate Synchronous DRAM. Like DDR SDRAM, QDR transfers data on the rising and falling edges of the clock signal. Unlike DDR, its read and write functions have a separate clock and port, so they can operate simultaneously. The newer QDR II has bus speeds up to 333 MHz as of 2005.
- QBM – Quad-Band Memory. A modification of DDR to double its throughput. Commercial failure.
- XDR DRAM – Extreme Data Rate DRAM. 2005, Rambus. 32-bit, 90 nm technology with a bi-directional, 400+ MHz bus sampling memory 8 times per clock cycle for throughputs of PC9600 to PC16000. (Claims of 3.2+ GHz rates are multiplying the actual clock rate by 8.) Used in the Sony Playstation 3, but little success in the broader market.
- DDR2 (or DDR II) SDRAM – Introduced 2004. A dual-channel evolution of DDR that samples memory four times per system bus clock cycle. With a 64-bit, 100 to 300 MHz bus, module speeds range from DDR2-400 (PC2 3200) to DDR2-1200 (PC2 9600). DDR2 uses 1.8 V standard on 240-pin DIMM, 200-pin SO-DIMM, 244-pin mini-DIMM, and 172- or 214-pin micro-DIMM modules. The modules are not compatible with slots meant for the original DDR even if pin count is the same.
- FB-DIMM – Fully Buffered Dual In-line Memory Module. 2005 variant of DDR2 that buffers the data lines as well as, like registered memory, the clock and address lines. Up to eight FB-DIMMs can share a single high-speed serial bus to the motherboard’s memory controller, rather than having a separate memory bus for each module.
- DDR3 SDRAM – 2007 successor to DDR2 that doubles the prefetch buffer yet again, meaning 8 reads per system bus clock cycle. It uses 90 nm process, standard 1.5 V power, and a 64-bit bus with clock rates from 400 MHz (DDR3-800, PC3 6400) to 1400 MHz (DDR3-2800, PC3 22400). Its 240-pin DIMM and 204-pin SO-DIMM modules (no mini- or micro-DIMM yet as of 2011) aren’t compatible with DDR2 slots.
- DDR4 SDRAM – 2014. Debuted with 30 nm process. Uses 2133 to 4800 MHz clock (PC4 17000 to PC4 38400 MB/s), and 1.2V to 1.5V power with pseudo-open drain (POD) technology instead of the previous 1.5V standard. It has more efficient read, write, and refresh operations than DDR3, but poorer latencies. Form factor is 288-contact DIMM, or 256-contact SO-DIMM for laptops.
- DDR5 SDRAM – 2020. Uses 2000 to 4100 MHz clock (PC5 32000 to PC5 65600 MB/s) and nominal 1.1V power, though actual voltage is often higher. Form factor is 288-pin DIMM, or 262-pin SO-DIMM for laptops. DDR4 has longer latencies than its predecessor but compensates with higher clock speed; DDR5 continues this trend. To prevent installation in a DDR4 slot, with which they’re not compatible despite having the same dimensions and pin count, 288-contact DDR5 modules have a notch in the exact center instead of the slightly offset notch of DDR4.
- DDR6 SDRAM – Expected in 2026. Laptop versions will probably use the CAMM form factor.
- DRC
- Design Rules Check. An automated error-detection step in chip manufacturing.
- DRDoS
- Distributed Reflection Denial of Service. Not to be confused with DR-DOS (see DOS). A computer network attack to shut down a server by sending access request packets containing the target server’s spoofed address to many other servers. These servers, believing the target address is trying to establish a connection, will send it a series of response packets with (this is key) significantly more data than the original request, amplifying the bandwidth controlled by the attacker. If enough servers can be duped into doing this, they overwhelm the target.
- This attack is fiendishly hard to deal with, because it can use an almost unlimited number of attack paths, and the duped servers don’t notice that they’re doing anything unusual. Compare DoS, DDoS.
- DRDRAM
- Direct Rambus Dynamic Random Access Memory. See DRAM, Rambus.
- DRFM
- Digital Radio Frequency Memory. A system that can digitally capture and reproduce a RF signal. Used for radar jamming and possibly for cognitive radio (see SDR).
- driver
- Short for device driver.
- DRM
- Digital Rights Management, although critics call it “digital restrictions management”, the same kind of hostile renaming used for the related concept of IP. Any digital copy-prevention technology. See DMCA, DVD, HDCP, MPA for examples.
- DRO
- Dielectric Resonator Oscillator. An oscillator that uses a short cylinder of dielectric as the resonant medium. It’s common at high microwave frequencies.
- DRSN
- Defense Red Switch Network. Worldwide US military system for exchanging classified data. See CCSS.
- DRT
- Digital Receiver Technology. See dirtbox.
- DS-#
- A set of AT&T digital carrier standards used in North America. They’re commonly called T-1, T-2, etc., but the T-# designations properly refer to just the physical channel standards for the signals. DS-0 is the basic 64 kb/s PCM voice-grade channel signal. DS-1 is 24 DS-0 channels, total 1.544 Mb/s. DS-1 data is sent in 193-bit TDM frames (24 channels × 8 bits/channel, plus 1 framing bit), at 8000 frames per second using RZ-AMI signaling.
- The DS-1 carrier can group every 12 frames as a superframe, using the LSb of each channel in the 6th and 12th frames for overhead, or can group every 24 frames into an extended superframe (ESF) that uses just the framing bits for overhead. A DS-1C is 3.152 Mb/s (two DS-1 carriers, plus overhead), a DS-2 is 6.312 Mb/s (four DS-1 carriers, plus overhead), a DS-3 is 44.736 Mb/s (seven DS-2 carriers, plus overhead), and a DS-4 is 274.176 Mb/s (six DS-3 carriers, plus overhead).
- Compare E-#, J-#. See also DUV and SONET.
- DSA
- Directed Self-Assembly. A method of creating microscale and nanoscale structures, using chemical processes to trigger the steps.
- DSB
- Dual Sideband. See SSB.
- DSC
- Dye-sensitized Solar Cell. A thin-film solar cell that uses a photosensitive dye on a semiconductor with wide band gap to produce electricity from visible light. It’s not as efficient as a conventional solar cell, but is expected to be the basis for solar windows.
- DS-CDMA
- Direct Sequence Code Division Multiple Access. A longer name for CDMA.
- DSF
- Dispersion Shifted Fiber. Optical fiber designed to exhibit zero dispersion in the wavelength window around 1.55 µm.
- DSL or xDSL
- Digital Subscriber Line. Any of several technologies that phone companies use to provide high-speed Internet service over existing lines. Compare cable modem. See also broadband.
- Modern telephone channels are digital, sending at 64 kb/s, except in the so-called “last mile” to each subscriber over old twisted-pair copper lines. The original solution for moving digital data over subscriber loops was a modem at each end, converting between digital data and analog line signals. Besides tying up the telephone line, this meant a very slow connection by modern standards – see the data rates of the V.## series voice-grade channel modems. What’s more, the connection would crash and require re-connection if anyone picked up a telephone extension.
- Data service providers, who have taken to calling the subscriber line the “first mile” to show how customer-oriented they are, have come up with several all-digital routes across it. Technically, this includes ISDN, but “DSL” usually means just the family of xDSL technologies listed below.
- ADSL – Asymmetric DSL. Signal encoding, compression, and modulation tricks allow downstream (i.e., from the central office to the subscriber) data rates of approximately 8 Mb/s in a 25-1104 kHz passband, and roughly 1 Mb/s upstream rates in a 25-138 kHz band. The actual rate achieved varies with the length of the subscriber loop, among other factors. On an 18,000 foot loop, ADSL offers T1 downstream rates (1.544 Mb/s). Downstream data signals all originates at the same amplitude, minimizing crosstalk. Upstream signals are variable in amplitude, but their lower frequency also reduces crosstalk. Some implementations of ADSL have the downstream and upstream signals sharing the same part of the channel, and rely on echo cancellation (EC) to prevent them from interfering with one another. Most implementations instead use FDD to separate the two. The signal encoding is CAPM or DMT (CAPM versions might be called Rate-Adaptive DSL, or RADSL). ADSL systems must go through the telco, and of course can talk only to other ADSL transceivers. They require a POTS splitter on the phone line to break out the 4 kHz voice traffic from the data traffic, routing the former through a LPF to the subscriber telephone or central office POTS switch and the latter through a HPF to the subscriber ADSL connection or central office ADSL mux.
- HDSL – High-bit-rate DSL. A scheme to transmit full-duplex T1 rates (1.544 Mb/s in both directions). The basic HDSL uses TWO twisted-pair lines, 2B1Q modulation, and a 0-370 kHz passband. HDSL2 uses just one twisted pair, 16-level trellis-coded PAM, and overlapping downstream and upstream passbands (0-440 kHz and 0-300 kHz respectively). HDSL4 uses two pairs, 16-level trellis-coded PAM, 0-130 kHz upstream passband, and 0-400 kHz downstream passband.
- RADSL – Rate-Adaptive DSL. See ADSL entry above.
- SDSL – Symmetric DSL. An AT&T design that supports full-duplex rates up to 2320 kb/s on a single UTP line. It uses 2B1Q modulation, and a 0-700 kHz passband. On longer loops, the maximum rate drops – about 160 kb/s at 23,000 feet, or 400 kb/s at 21,000 feet.
- VDSL – Very-high-bit-rate DSL. An emerging standard that supports approximately 22 Mb/s downstream and 13 Mb/s upstream rates on a single UTP line. It uses DMT or QAM modulation and a passband from 25 kHz to 12 MHz. Higher rates have been proposed for shorter loops. As usual, longer loops mean lower rates.
- G.fast – Official name ITU-T G.9700. A developing (2014) standard using up to about 106 MHz bandwidth to achieve a theoretical maximum throughput of 1 Gb/s. Actual rates will be less. The copper link can’t exceed about 250 meters, and G.fast will have increasing problems with crosstalk and possible interference with the commercial FM radio band. An extension called XG.fast, using 500 MHz of bandwidth, reaches 10 Gb/s in lab tests over 30-meter copper cable.
- Crosstalk between unshielded twisted pair (UTP) lines is negligible at voice frequencies, but for xDSL, it becomes the major limitation on transmission speed. This is especially true when different xDSL technologies are present in different lines on the same cable.
- DSLAM
- Digital Subscriber Line Access Multiplexer. A multiplexing switch at the phone company central office that connects DSL-enabled customer circuits to the Internet.
- DSLR
- Digital Single-Lens Reflex. A digital camera that uses SLR to display the lens image to the photographer.
- DSM
- Deep Sub-Micron. An old term referring to circuits with elements smaller than 0.5 µm, which is virtually all of them now.
- DSN
- (1)
- Defense Switched Network. A comms system linking DoD facilities worldwide. Its largest component is non-secure telephones, but it supports Secure Telephone Units (STU), the Defense Red Switch Network (DRSN), and two computer networks called Unclassified IP Router Network (NIPRNet) and Secret IP Router Network (SIPRNet).
- (2)
- Deep Space Network. A system of NASA installations – one in the Mojave Desert, one in Spain, and one in Australia – that support radio astronomy and communicate with spacecraft.
- (3)
- Delivery Status Notification. A function of E-mail protocols.
- DSP
- Digital Signal Processor (or Processing). A DSP chip is a microprocessor optimized for math-intensive, discrete-time signal processing, and it supports complex instructions to perform typical signal processing computations quickly. These complex instruction sets make it difficult to create efficient high-level language compilers for DSPs, so the traditional way to program DSPs is in assembly language. More and more, however, libraries and APIs are being used instead. As of 1998, the four top makers of DSP chips are Analog Devices, Lucent Technologies, Motorola, and Texas Instruments.
- DSP-enhanced general-purpose microprocessors can serve as DSP chips, but they cost much more, use far more power, have less predictable execution times (due to caching and superscalar architecture), and lack DSP development tools. On the other hand, they have better software development tools, and usually maintain compatibility between generations, so they are increasingly competing with traditional DSPs.
- DSP~LINK3
- An open standard created by Spectrum Signal Processing Corp. for a secondary, asynchronous master-slave bus interface to Industry Pack (IP) modules. The data rate, typically 25 MB/s, is usually determined by the slave.
- DSSS
- Direct Sequence Spread Spectrum. One of two types of spread-spectrum radio (FHSS is the other), common in wireless networks for sending multiple signals in a shared band. The sending station XORs each data signal with its own chipping code, or spreading code: an orthogonal, pseudo-random binary sequence repeating at a bit rate (chip rate) that’s a whole-number multiple (the spreading ratio) of the raw data rate. It transmits the resulting XORed sequence using FSK or PSK modulation.
- The signal’s spectrum is spread over the whole band because it’s set by the chip rate instead of the lower data rate. The receiving end uses the same chipping code to pick out the data, with any other DSSS signals in the same band treated as random noise. The chip rate is often characterized in chips/second (cps) rather than b/s or Hz. See 802.11, CDMA.
- DSU
- Data Service Unit. A simplified modem that transmits digital data over a private line, or over short distances through public lines. It converts data to a bipolar format for transmission. See CSU.
- D-sub
- D-subminiature. “D” refers to the shape of the connector. Members of this family of cable connectors, used for many types of signals including the ubiquitous PC serial ports with RS-232 signaling, are popularly but incorrectly called DB-9, DB-15, etc. “DB” is just one of five standard shell sizes, each of which can accommodate a varying number of pins or sockets. The correct name is determined as shown below by the shell size, the number of contacts, and whether the contacts are male (P = pins) or female (S = sockets). For example, a typical PC parallel port is DB-25S, while a PC serial port is either DE-9P (the IBM AT standard) or DB-25P (the older IBM XT standard). High-density connectors are sometimes called HD-## or HDx-##, such as the HD-15 connector used for analog VGA graphics. Some sources use M for male instead of P for pin, and F for female instead of S for socket.
- There are combination connectors, such as the 13W3, that use one of the above configurations but replace some of the pins or sockets with coaxial, high-current, or high-voltage contacts. Also, the MIL-C-83513 standard specifies D-microminiature or micro-D connectors, with 9, 15, 21, 25, 31, or 37 contacts in 2 rows or 51 contacts in 3 rows, and 0.050" spacing. It’s easy to mistake the MIL-C-83513 male plug for a female socket, and vice-versa; the plug pins are recessed in a plastic housing, while the socket shafts stand unsupported like pins.
- DSVD
- Digital Simultaneous Voice & Data. An obsolete V.34+ modem protocol that allows voice and data to pass through a telephone line simultaneously. The voice signal is compressed, but its presence still drops the expected data rate to 19.2 kb/s.
- DTD
- Document Type Definition. The schema to which a HTML, XHTML, or other SGML-derived document conforms, specified in the first line of the file with a unique label called a formal public identifier (FPI). HTML has three DTDs: Strict, Transitional, and Frameset.
- DTE
- Data Terminal Equipment. A data source or sink, e.g. a computer, that’s part of a data transmission system. Contrast DCE.
- DTFT
- Discrete-Time Fourier Transform. See Fourier transform.
- DTMF
- Dual Tone Multi-Frequency. The audio signaling frequencies produced by a touch-tone phone’s keypad. Each button emits two distinct tones to minimize the chance of false dialing.
- DTR
- Desktop Replacement. A powerful, relatively bulky notebook PC mainly for business users, to provide the capabilities of a workstation with the portability of a notebook. This compromise approach means higher cost and shorter battery life.
- DTV
- Digital Television. TV transmitted with digital rather than analog modulation. In the US, NTSC-format analog TV officially went off the air in 2009. Analog TVs require a D/A tuner circuit to get ATSC-format digital TV. See also DVB and ISDB.
- dual-homed
- See multi-homed.
- duo-binary signaling
- The simplest form of partial response modulation.
- duplexer
- See circulator.
- Duron
- See AMD.
- DUT
- Device Under Test. Also called unit under test (UUT).
- DUV
- (1)
- Digital Under Voice. An old telco scheme for running digital data in the empty 0-386 kHz spectrum below an analog trunk line’s FDM Basic Master Group. It carried 1.544 Mb/s, which became the DS-1 standard.
- (2)
- Deep Ultra-Violet. Refers to a range of EM wavelengths used for IC lithography. Sources vary on what that range is, but 100 to 300 µm is in the ballpark. The newer EUV lithography can create much smaller feature sizes, but is much more complex and expensive.
- DVB
- Digital Video Broadcasting. A European standard for digital TV (DTV). It uses a multiple-carrier modulation scheme called COFDM that divides the 8 MHz channel into several thousand subchannels, each carrying a portion of the 24 Mb/s digital signal. Includes DVB-T (terrestrial), DVB-C (cable), DVB-S (satellite), and DVB-RCS (return channel via satellite). Compare ATSC, ISDB.
- DVD
- Digital Versatile (originally Video) Disc. An outgrowth of CD technology, used to store movies or other large quantities of digital data. An open file system specification called Universal Disc Format (UDF) supports the various formats listed below, and most optical drives and players/recorders can translate between them, with occasional compatibility problems. Consequently, these rival standards – while annoying – have caused less trouble than the Betamax/VHS and HD-DVD/Blu-Ray schisms, and will probably persist until solid-state devices kill off the DVD. Warning: video DVDs are encoded for a specific TV system (NTSC or PAL/SECAM).
- DVD Audio – An audio disc, intended to supplant music CDs.
- DVD Video – For movies, read-only. Can hold about 17 GB (8 hours of video) if two layers on both sides are used.
- DVD-ROM – Essentially DVD Video for data, with support for computer file formats. Intended to supplant CD-ROM for distributing software.
- DVD-R – In 1995, a group of 10 companies founded the DVD Consortium, which renamed itself the DVD Forum in 1997. They created this standard for a write-once disc with 4.7 GB (more precisely 4,707,319,808 bytes) capacity, intended for video. DVD-RW is a rewriteable version with the same capacity. The DVD-R DL (double layer) disc has two data layers that together hold 8.5 GB (8,543,666,176 bytes). Its write speed is considerably slower than that of a single-layer disc. And, of course, there’s the DVD-RW DL rewriteable double layer.
- DVD+R – In 1997, Philips, Sony, and Thomson split from the DVD Forum to found the DVD+RW Alliance, which backs this standard. It’s very similar to DVD-R, with nearly identical capacity (4,700,372,992 bytes, or, for double-layer DVD+R DL, 8,547,991,552 bytes). Also like DVD-R, it comes in rewriteable DVD+RW and DVD+RW DL.
- DVD-RAM – Supported by Toshiba, Hitachi, & Panasonic. A rewriteable disc intended for removable data storage. More robust than DVD-RW and DVD+RW, but less well suited to playing video. Originally 2.6 GB capacity, now 4.7 GB per side. Single-side discs come in removable Type 2 cartridges, and dual-sided discs in sealed permanent Type 1 cartridges that make them incompatible with other DVD types.
- Corporate greed alert: Entertainment conglomerates have created 8 DVD region codes (6 regions of the world and 2 special codes). Equipment made for one region will not play a DVD encoded for another. Most DVD players now on the market have region control built in, although multi-region and region-free players exist. A DVD should have the region code on the package somewhere. The USA & Canada are Region 1. Also, the Macrovision technology is applied to the coding on many DVDs. A Macrovision-enabled DVD player will distort the analog output from such a DVD to prevent copying to a VCR. Finally, there’s a newer system called Regional Coding Enhancement (RCE) that prevents DVDs encoded with it from playing on region-free DVD players. Workarounds exist for all these.
- DVI
- Digital Visual Interface. See graphics.
- DWDM
- Dense Wavelength Division Multiplexing. Transmitting multiple carriers at different wavelengths on a single fiber – essentially FDM at optical frequencies. This requires broadband optical amplifiers (EDFAs) rather than regenerating repeaters, which would have to demux and remux the signal.
- Optical fiber’s minimum attenuation of ~0.2 dB/km occurs for wavelengths of about 1550 nm, so the original EDFA operated on a band centered at 1550 nm. This technology was crucial to the growth of the Internet, by dramatically increasing the maximum bandwidth of installed fiber. In 1995, 4-channel WDM was introduced. Systems have since achieved 160+ channels, and the industry has taken to calling it DWDM.
- DWDM channels are spaced about 100 GHz (0.8 nm) apart, referenced to 1552.5 nm (193.1 THz). NRZ optical modulation is performed by either directly modulating input current to a diode laser (best for under 1 Gb/s), or using a modulator to chop the laser’s beam (good up to about 100 Gb/s). Above 100 Gb/s, things get tricky. Rates above 1 Tb/s have been demonstrated in labs.
- Increasing the number of channels eventually calls for better fiber, such as Lucent’s NDSF, and wider-bandwidth EDFAs. See OXC, OADM.
- DWEM
- Dead White European Male. The Enlightenment and its aftermath in Europe produced a series of brilliant men whose names are commemorated in key principles of math and engineering. A disproportionate number of them were French: René Descartes (1596-1650), Pierre de Fermat (1601-1665), Blaise Pascal (1623-1662), Charles Augustin de Coulomb (1736-1806), Joseph-Louis Lagrange (also claimed by Italy, 1736-1813), Pierre-Simon Laplace (1749-1827), Jean Baptiste Joseph Fourier (1768-1830), André Marie Ampère (1775-1836), Siméon Denis Poisson (1781-1840), Augustin Jean Fresnel (1788-1827), Augustin Louis Cauchy (1789-1857), Nicolas Léonard Sadi Carnot (1796-1832), Evariste Galois (1811-1832), and Jules Henri Poincaré (1854-1912).
- From what is now Germany came Johannes Kepler (1571-1630), Gottfried Wilhelm von Leibniz (1646-1716), Johann Carl Friedrich Gauss (1777-1855), Friedrich Wilhelm Bessel (1784-1846), Georg Simon Ohm (1789-1854), Johann Peter Gustav Lejeune Dirichlet (1805-1859), Georg Friedrich Bernhard Riemann (1826-1866), and Heinrich Rudolf Hertz (1857-1894). Franz Ernst Neumann (1798-1895) and Gustav Robert Kirchhoff (1824-1887) were nominally German too despite being born in what are now the Czech Republic and Russia, respectively. From England came Isaac Newton (1643-1727), Thomas Bayes (1702-1761), Michael Faraday (1791-1867), Charles Babbage (1791-1871), George Boole (1815-1864), James Prescott Joule (1818-1889), John William Strutt, Lord Rayleigh (1842-1919), Oliver Heaviside (1850-1925), and John Henry Poynting (1852-1914); from Scotland, James Watt (1736-1819), William Thomson, Lord Kelvin (1824-1907), and James Clerk Maxwell (1831-1879); from what is now Italy, Evangelista Torricelli (1608-1647), Alessandro Giuseppe Antonio Anastasio Volta (1745-1827), Amedeo Avogadro (1776-1856), and maybe Lagrange; from Austria, Christian Andreas Doppler (1803-1853), Ernst Mach (1838-1916), and Ludwig Boltzmann (1844-1906); from Serbia, Nikola Tesla (1856-1943); and from Switzerland, Leonhard Euler (1707-1783) and the awful Bernoullis.
- This is not a complete list.
- DWF or .dwf
- Drawing Web Format. This newer file format is for creating drawings to be used on the Web. It contains features that allow users to view it without AutoCAD.
- DWG or .dwg
- The standard AutoCAD drawing file format. It has changed with successive releases of AutoCAD.
- DWMT
- Discrete Wavelet Multi-Tone modulation. A variant of DMT using wavelets.
- DWT
- Discrete Wavelet Transform. The wavelet equivalent of the discrete Fourier transform.
- DX
- Under Intel, see 80386, 80387, 80486, 80487.
- DXF or .dxf
- Drawing Exchange Format. This file format standard was originally created by AutoDesk to represent 3D models and scenes in AutoCAD. It’s used by many CAD and graphics programs, although different programs might display an object in different ways. As with DWG formats, DXF formats vary from one software release to the next.
- dynamo
- A machine for producing electric power inductively from rotary motion, with a feedback cycle in which the machine’s output powers its electromagnets, and the stronger electromagnets further boost power output. In modern usage, this broad description tends to be called just a generator. (Also, see alternator.) “Dynamo” has taken on the specialized meaning of a DC generator: it puts the magnet(s) in the fixed stator and the conducting coil in the rotor, and employs a ring commutator on the rotor shaft to convert the output AC into pulsed DC. Mechanical tricks, such as multiple coils with split-ring commutators, can smooth the DC levels.
- The dynamo as a DC source is becoming rare, because modern solid-state rectifiers and switching regulators are more efficient than commutators.
| 0 dB | Threshold of human hearing |
| 20 dB | Whisper at 1 meter |
| 40 dB | Quiet office or residential area |
| 60 dB | Normal conversation, background music |
| 80 dB | Ringing telephone |
| 100 dB | Motorcycle |
| 120 dB | Jackhammer |

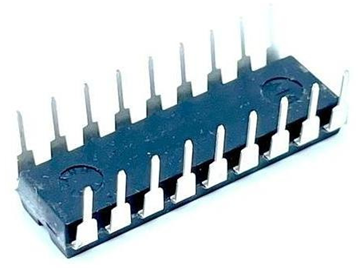
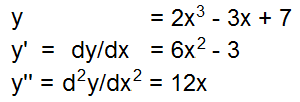
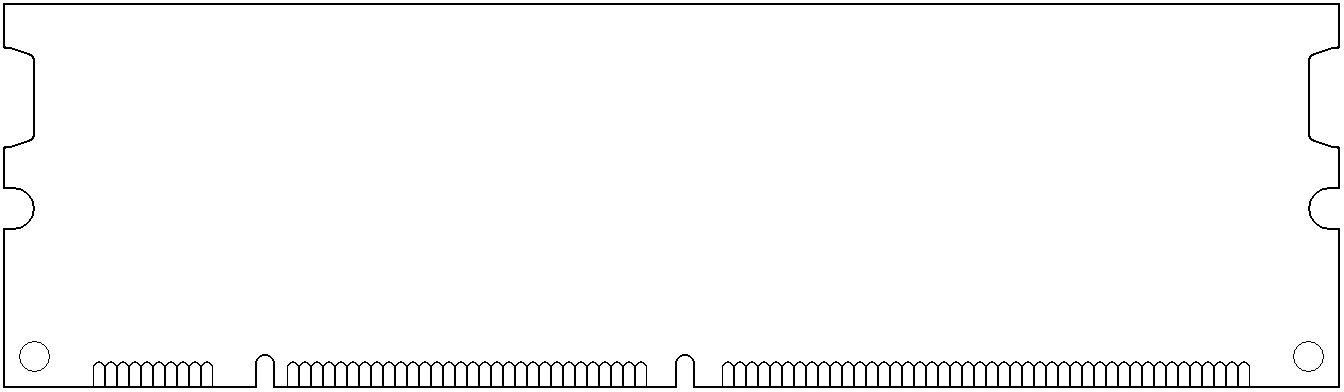
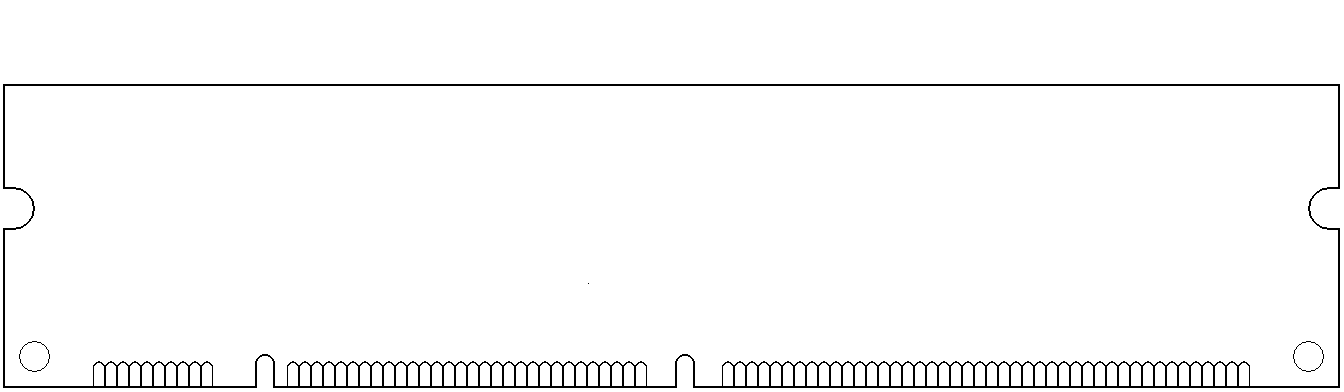
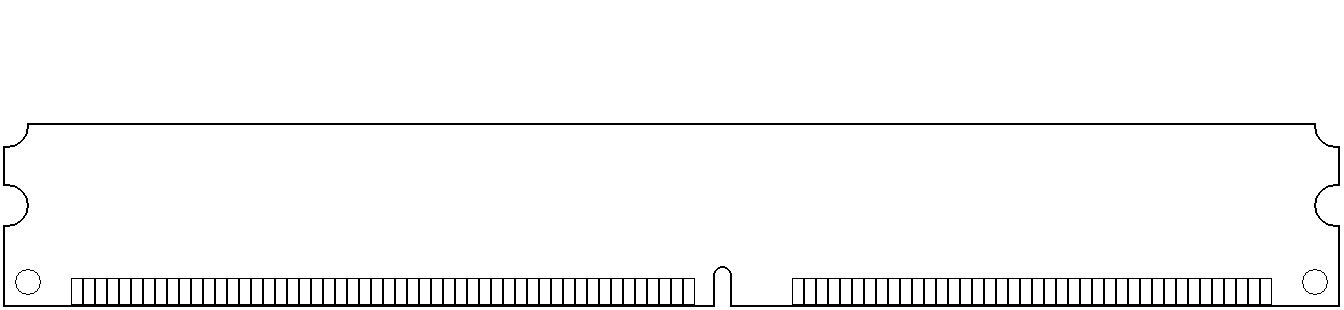
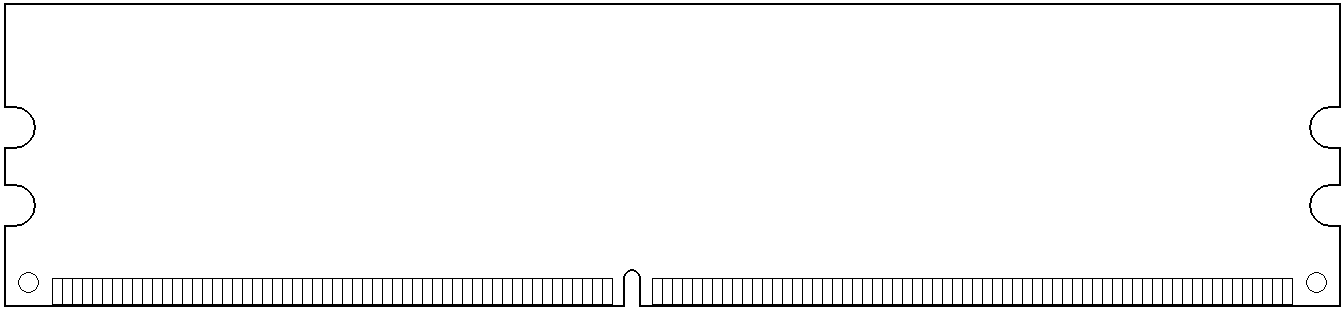
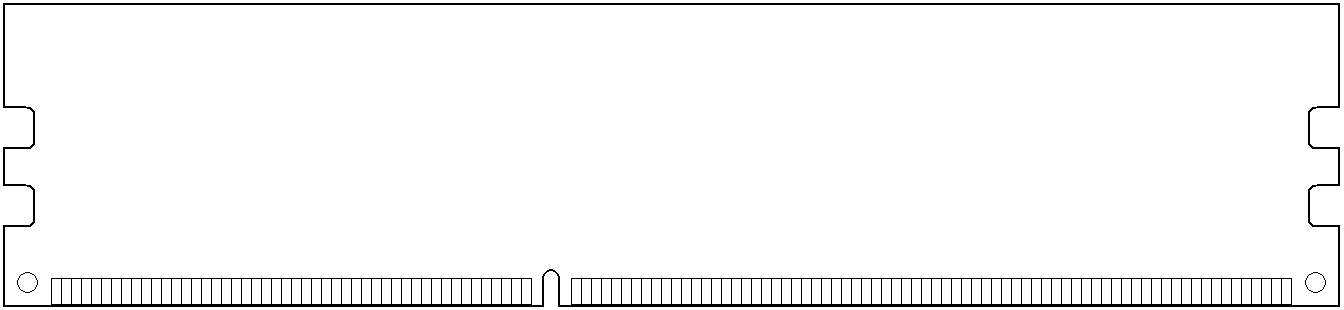
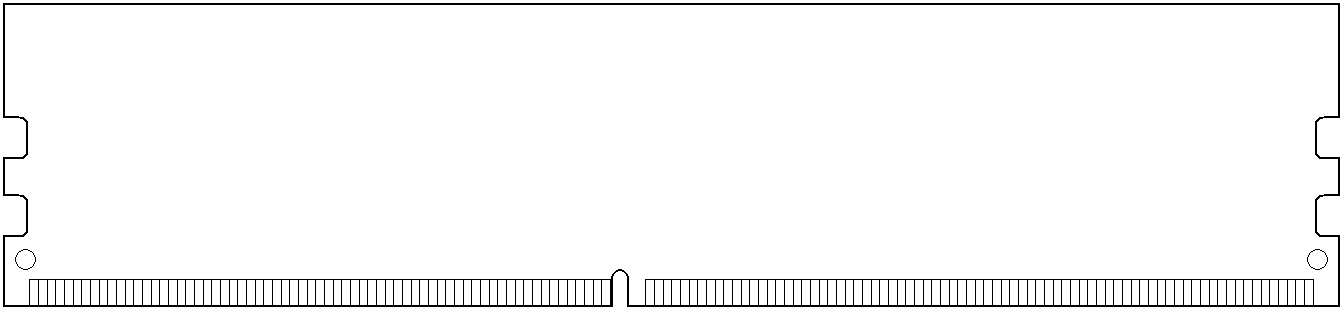
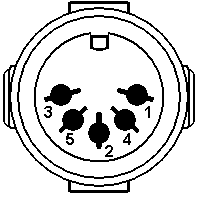
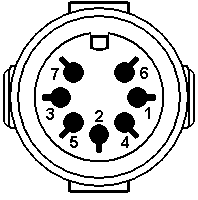
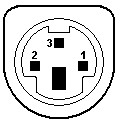
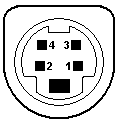
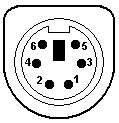
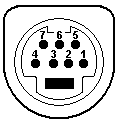
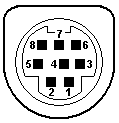
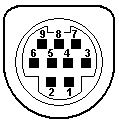
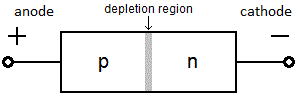
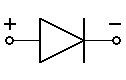
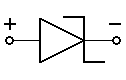
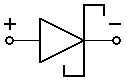
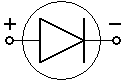
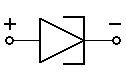
Schematic symbols for diode types
| .au | Australia | .de | Germany | .ie | Ireland | .nl | Netherlands | .uk | United Kingdom | |||||
| .br | Brazil | .es | Spain | .in | India | .nz | New Zealand | .za | South Africa | |||||
| .ca | Canada | .fi | Finland | .it | Italy | .ru | Russian Federation | |||||||
| .ch | Switzerland | .fr | France | .jp | Japan | .se | Sweden | |||||||
| .cn | China | .hk | Hong Kong | .mx | Mexico | .tw | Taiwan |
| Shell | 2-row (0.108" spacing) | 3-row (high-density) | double-density |
| DE- | 9 | 15 | 19 |
| DA- | 15 | 26 | 31 |
| DB- | 25 | 44 | 52 |
| DC- | 37 | 62 | 79 |
| DD- | 50 (3-row) | 78 (4-row) | 100 (4-row) |