- backchannel
- A separate data signal that uses the same channel as a larger signal. Voice-grade channel modems (see V.##) use them as a dedicated path for ACKs, ACK requests, suspend-transmission requests, and other control data.
- More recently, “backchannel” has come to mean a connection to a remote server that installed software establishes autonomously, often without the user’s knowledge or permission, when a computer connects to the Internet. This trick is a standard feature of malware, although major software companies do it too. Malware backchannels contact a P2P site, social networking site, IRC chat room, malicious (or pirated) HTTP site, etc., to pass data to and receive commands or additional code from the malware author. The traffic will often be encrypted and sent via TCP/IP port 443, which is for SSL or TLS connections.
- backdoor
- A way to access a networked system without the user’s knowledge or permission. Normally this refers to a hidden account or vulnerability built in by a designer, programmer, or manufacturer, but it can also mean an opening created by malware.
- backplane
- Generically, a computer data bus that accepts plug-in devices. The standard PC uses an active backplane, meaning it’s on a motherboard along with the CPU and accepts only peripherals. This design restricts the user’s ability to reconfigure and upgrade the system. A passive backplane provides backplane slots for all the system devices, including the CPU itself on a SBC card (although slots for SBC cards require additional special connectors). The backplane bus can be PCI, one of its descendants, VME, etc.
- Hard drive backplanes are a different issue. They accept multiple hard drives on a SCSI or ATA bus.
- BACnet
- Building Automation and Control Networks. An ISO-approved, IP-compatible network communications standard for controlling a building’s mechanical and electrical systems, particularly HVAC. There’s a rival standard called LonWorks (from Local Operating Network).
- BACP
- Bandwidth Allocation Control Protocol. Part of PPP.
- balun
- Balanced to Unbalanced. A device used to prevent EMI problems arising from the connection between a balanced (differential) line, e.g. a twisted pair or a center-fed antenna, and an unbalanced (signal referenced to ground) line, e.g. a coaxial cable. For example, a coaxial cable attached to an antenna could act as part of the antenna and radiate.
- There are two types of balun: the choke balun and the transformer balun. The choke balun blocks RF current at the feed point by creating a large series impedance on the outside of the cable (i.e. in the shield). Coiling the cable will have this effect, as will feeding the cable through ferrite beads or tubes. It won’t work well on a high-impedance circuit, though. Where the choke balun merely suppresses surface currents, the transformer balun acts to create balance by forcing equal and opposite currents on both sides of the feed point.
- banana plug
- Banana plugs and jacks, named for the shape of the plugs but sometimes called 4mm connectors, are ubiquitous in electrical test equipment and labs. The plugs are made with either 4 or 9 of the bulging metal strips (also called leaves) that ensure a tight fit with the jack. They’re typically rated for up to 5, 10, or 15 amps, but the tolerance depends on design and quality. Some have a plastic shroud for safety.
- BAP
- Barometric Absolute Pressure. Refers to normal air pressure or sensors that measure it, as opposed to MAP.
- Bash
- Bourne-Again Shell. The name is a riff on the 1979 Bourne shell written by Stephen Bourne. A command-line interface (CLI) – aka shell program – for Unix and related operating systems, created in the 1980s as part of the GNU freeware project. It’s become the standard tool for Linux programs to run OS command scripts.
- BASIC
- Beginner’s All-purpose Symbolic Instruction Code. See programming language.
- battery
- Strictly speaking, a group of identical units (cells) working together in series or in parallel to produce electric current. The vast majority are galvanic batteries with cells that use enclosed oxidation-reduction reactions, although there are other technologies, such as nuclear batteries. The 12-volt lead-acid car battery, with its six 2V cells in series, is a true battery. So is the much smaller 9V alkaline battery, aka the PP3, with six 1.5V AAAA cells in series. The commercial AAA, AA, C, and D cells are single cells, technically not batteries, but are called batteries anyway.
- Cells in series produce higher voltage, while those in parallel (preferably with diode isolators to protect the rest if one cell fails) produce higher current. Mismatched cells should not be connected in series, because the stronger cells deplete the weakest and drive it into cell reversal, potentially rupturing it. Mismatched cells in parallel aren’t a hazard, but have uneven depletion.
- A primary battery is one intended to be used until consumed. A secondary battery is rechargeable. A reserve battery, which can in construction be a primary or a secondary, is the normally-idle backup for a main power source. Primaries tend to have the greater energy density, but secondaries can drive higher currents – so much so that many have built-in fuses or current limiters for safety. Secondaries are also more expensive.
- A flow battery is a very large industrial battery that stores charge in two different liquid electrolytes, which are kept in external tanks. It discharges and charges via a voltage stack with an ion-conducting membrane between the circulating electrolytes. This makes it similar to a fuel cell, except that its “fuel” requires recharging rather than being consumed.
- Galvanic batteries are described by the reactants they use to create current. Most of these reactions are reversible, hence can be used for rechargeable batteries (but as a rule, batteries are not rechargeable unless the packaging explicitly says so):
- alkaline – Most AAA, AA, C, and D cells in consumer electronics are non-rechargeables based on alkaline rather than acidic chemistry. Nowadays, it’s the oxidation of zinc by manganese dioxide. Rechargeable alkaline cells are relatively cheap compared to other rechargeables, but also have lower maximum current and shorter lives.
- graphene aluminum-ion – In R&D as of 2021, using layers of graphene with embedded aluminum atoms. Claimed to offer major advantages in capacity, charging speed, cost, and safety over lithium-ion batteries.
- lead-acid – The oldest battery type still in commercial use, notably for automobile ignition systems because of its high current capacity. It uses the reaction between lead and sulfuric acid, H2SO4.
- Li-ion – Lithium Ion. Uses some lithium compound for the cathode, e.g. Li-NCA (nickel-cobalt-aluminum), Li-NMC (nickel-manganese-cobalt), or LFP (lithium-iron-phosphate, F standing for Fe). Different cathode compositions are suited to different applications, and not all of them are rechargeable. The cathode designation can be followed by numbers indicating the relative proportion of each element or compound; for example, NMC811 means 80% nickel, 10% manganese, 10% cobalt, but NMC111 means equal amounts of each. Lithium ions transport electrons from the cathode across a liquid electrolyte to combine with the anode, which is usually graphite, where they release the electrons to produce current.
- Li-ion batteries have higher specific energy (energy-to-weight ratio) than other chemistries, and hold charge well when idle, which has led to them replacing the older NiCd and NiMH, and even lead-acid batteries for some vehicle uses. On the down side, cold or very hot climates degrade their performance, and they’re susceptible to thermal runaway: tiny defects cause short-circuits between cathode and anode, the heat of the short-circuits creates more defects, which cause more shorts, until the battery spontaneously bursts into flame, or even explodes due to rapid build-up of gases.
- lithium-metal – Refers to any of a number of solid-state designs with a lithium anode and a metal alloy cathode. These can achieve even higher energy density than Li-ion, and don’t have the latter’s problems with thermal runaway, but as of 2024 are too expensive to be commercially viable.
- LMR – Lithium Manganese-Rich. A technology intended for EVs and in development as of 2025, promising improved energy density and lower cost. It eliminates expensive cobalt from the design, while using more manganese, which is relatively cheap.
- Na-ion – Sodium Ion. Similar in design to the various types of Li-ion batteries but with lower energy density and greater weight. On the plus side, they use elements that are more widely available and much less environmentally harmful to obtain, and they can withstand many more charge cycles.
- NiCd – Nickel-Cadmium. Based on electrodes of nickel oxyhydroxide (NiOOH) and cadmium. Not much used anymore, partly because cadmium is toxic and expensive, partly because of thermal issues.
- NiMH – Nickel-Metal-Hydride. Uses electrodes of nickel oxyhydroxide (NiOOH) and any of a number of hydrogen-attracting metal alloys. The newer LSD (low self-discharge) types have a significantly longer shelf-life, comparable to that of non-rechargeable alkaline batteries.
- SLA – Sealed Lead-Acid. A newer lead-acid design that eliminates spillage.
- zinc-air – This type’s reliance on abundant, non-toxic zinc means it’s safe and potentially cheap, but its reliance on oxygen from air has so far required that it use expensive precious-metal catalysts for discharging and recharging.
- zinc-carbon – One electrode is zinc; the other is a carbon rod surrounded with a mix of powdered carbon and powdered manganese dioxide. The electrolyte is a paste of zinc chloride or ammonium chloride. Unlike most battery chemistries, this one is not suited for recharging. Its use is in decline.
- The positive terminal of a battery is the cathode, and the negative terminal the anode. (These terms are reversed for a power-consuming circuit, which includes a battery when it’s being re-charged.) A car battery’s anode is tied to the engine block, because that serves as reference ground for the car’s circuits. When connecting jumper cables between car batteries, first connect a cable from positive cathode to positive cathode (the cathodes typically have red caps), then attach the second cable to the negative (black) anode of the stronger battery, and finally connect it to the chassis, rather than directly to the battery anode, of the car being jumped – closing the circuit creates a spark, which should be kept away from the battery in case it’s leaking hydrogen.
- baud
- Named for French engineer Jean-Maurice-Émile Baudot (1845-1903). A measure of the serial data transmission speed in symbols per second, NOT bits per second – the two are equal only in two-state systems such as BPSK and 2-FSK. The bandwidth of a signal tends to be roughly equal to its baud rate, which is also called its modulation rate or signaling rate.
- Baudot
- See data code.
- BB
- (1)
- Baseband. A signal prior to IR or RF modulation, or after RF and IF demodulation.
- (2)
- Broadband. See broadband.
- BBS
- Bulletin Board System (Service). A type of computer-hosted forum for users to log in and post announcements, comments, and downloadable files, as well as to play games, chat, or use other interactive content. Unlike the decentralized and network-aware Usenet, which came a few years later, the reach of a BBS is physically limited by being tied to a specific server.
- The BBS peaked in the 1980s, when users still had to connect over a phone line using a VGC modem and a terminal-emulation program. Despite the later addition of Telnet and even WWW interface capability, it has almost disappeared.
- BC
- Bus Controller. The controlling node on a MIL-STD-1553 data bus.
- BCCH
- Broadcast Control Channel. A logical channel in GSM that continually broadcasts, on the downlink, information such as base station identity, frequency allocations, and frequency-hopping sequences.
- BCD
- Binary Coded Decimal. A method for representing and manipulating decimal digits 0-9 using half a byte (a nibble), i.e. 4 bits. It’s easily confused with hexadecimal, which is just the base-16 reading of binary numbers, because the BCD and hexadecimal interpretations of a byte are the same if the nibble values don’t exceed 9. For example, 01000111 can be either the BCD value 47 or hexadecimal 0x47, which is 71; on the other hand, 10110110 can’t be a BCD value, so it’s hex 0xB6, which is 182.
- BCH
- Bose-Chaudhuri-Hocquenghem. A family of FEC cyclic block codes, named for its developers (no connection to either Bose stereo speakers or Bose-Einstein condensates). BCH codes are a generalization of the simpler Hamming codes.
- BCI
- Brain-Computer Interface. Still (2017) experimental, using EEG attachments.
- BCS
- Bardeen Cooper Schrieffer. See Cooper pair.
- BDF
- Building Distribution Frame. See distribution frame.
- BDM
- Background Debug Mode. An in-circuit debugging standard for embedded processors, created by Motorola. See also JTAG, Nexus.
- BDSL
- (1)
- Broadband Digital Subscriber Line. Outdated term meaning any DSL used for broadband connections.
- (2)
- Broadcast Digital Subscriber Line. Outdated term for using DSL to simultaneously transmit the same signal to many subscribers.
- BEC
- (1)
- Business E-mail Compromise. A breach of network security that starts with e-mail – a phishing attack, an e-mail attachment containing malware, an e-mail containing a link to a malware site, or a combination of these methods.
- (2)
- Bose-Einstein Condensate. Named for Indian physicist Satyendra Nath Bose and German physicist Albert Einstein, whose work predicted its existence, this is a state of matter that occurs when a thin cloud of bosons is cooled to near absolute zero. At this temperature, most of the bosons occupy the lowest quantum state, causing the cloud to behave in some respects like a single giant atom.
- BeiDou
- See satnav.
- Bell 103
- (1962) An asynchronous, 300 b/s voice-grade channel modem, equivalent to ITU’s V.21.
- Bell 212A
- A late 1970s synchronous/asynchronous, 1200 b/s, full duplex voice-grade channel modem, equivalent to ITU’s V.22.
- Bellcore
- Bell Communications Research. An R&D organization created in 1984 by the divestiture of AT&T, to be jointly owned & run by the RBHCs. It included much of the former Bell Labs; the rest became part of Lucent. It was acquired by SAIC in 1997, changed its name to Telcordia Technologies, was acquired by Ericsson in 2012 and renamed iconectiv, and was later sold yet again. Sic transit etc.
- BER
- Bit Error Rate. The ratio of erroneous bits to total transmitted data bits.
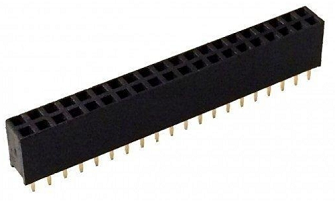
- Berg stick
- A cable connector or circuit board header consisting of one or two variable-length rows of unshrouded pins or pin sockets. The most common pin spacing for the headers is 2.54 mm (0.1 inch).
- BERT
- Bit Error Rate Test (or Tester).
- Bessel function
- The family of functions that solve x2[d2y/dx2] + x[dy/dx] + [x2 – n2]y = 0, the Bessel differential equation. These functions are used in analyzing wave equations, multiple-body motion, etc.
- beta particle
- An electron or positron, β- or β+, traveling at sufficient speed to be classed as ionizing radiation (IR). More penetrating and harmful than alpha particles. Sometimes called beta rays.
- BFF
- Binary File Format. An IBM file format.
- BFH
- Big Hammer. A crude but effective engineering tool.
- BFSK
- Binary Frequency Shift Keying. Two-state FSK.
- BGA
- Ball-Grid Array. See JEDEC.
- BGP
- Border Gateway Protocol. A member of the TCP/IP protocol suite at the Application layer, introduced in 1989 to replace the older EGP (Exterior Gateway Protocol). Internet gateway servers use it to describe their access and routing capabilities to other servers, to enable optimal routing. Because BGP is based on trust – the assumption that servers using it won’t lie – it can be abused to block or intercept network traffic, directing it somewhere it’s not supposed to go.
- In 2014, the number of Internet routes exceeded 219. Many older Internet routers had enough TCAM memory for “only” 219 entries, and responded by crashing or ignoring new routes.
- bias tee
- A three-port connector that adds a DC component to or extracts it from a signal. It can be used, for example, to supply DC power to a device through the RF input.
- BiCMOS
- Bipolar Complementary Metal Oxide Semiconductor. A technology that incorporates analog bipolar (i.e. transistor) and digital CMOS devices on a single IC. It can use ECL or TTL signal levels.
- BiFET
- Bipolar Field Effect Transistor. A technology that incorporates analog bipolar (i.e. transistor) and unipolar FET devices on a single IC.
- big-endian
- See endian.
- binary
- As an adjective, this means having two states: 1/0, on/off, up/down, yes/no, true/false, positive/negative, full/empty, etc. Digital computers, with very rare and unimportant exceptions, use binary code for their files and signals, because anything else – trinary, quaternary, etc. – would add complexity without any compelling advantage. Although all computer files are, therefore, ultimately binary, “binary” as a noun means a file that has no higher-level formatting (i.e., representing text characters) for most or all of its content. This kind of binary-only content, also called machine language, consists of data and executable programs.
- binary logic
- Also called Boolean logic, for English mathematician George Boole (1815-1864). The set of discrete mathematical operations that digital computers use because, unlike decimal math, they can be implemented by transistor circuits. Besides the basic AND and OR operations, and NOT (the inverting operator), there are the hybrid operations NAND (not-AND), NOR (not-OR), XOR (exclusive-OR), and XNOR (exclusive-not-OR). Their outcomes for any given pair of input bits a and b are shown by the appropriate truth table:
- As shown, binary operations follow the commutative property – the order of the inputs doesn’t matter. AND, OR, and NOT as operators are represented in the C programming language by the symbols &, |, and ! respectively, but in text they and the other operators are normally written in full. XOR is sometimes represented with the ⊕ symbol (see modulo-2, also twos-comp).
- In logic diagrams, the logic gates that perform these operations are represented with the symbols shown above. The examples show two bits of input (except NOT, which can accept just one), but gates with three or more inputs are common. Compare fuzzy logic.
- In addition to those logical operations, there are the shift operations. Their terminology uses the arbitrary convention that the most significant (MS) bits of a fixed-length binary sequence are on the left, and the least significant (LS) on the right. With that in mind, the shifts are:
- LSL – Logical Shift Left. The bits are shifted some number of places up toward the most significant bit. The MS bits shifted out are discarded, and the LS bits shifted in are zeroes. ASL (arithmetic shift left) means the same thing.
- LSR – Logical Shift Right. The bits are shifted some number of places down toward the least significant bit. The LS bits shifted out are discarded, and the MS bits shifted in are zeroes. This is the mirror image of LSL. It is not the same thing as ASR.
- ASR – Arithmetic Shift Right. The bits are shifted some number of places down toward the least significant bit. The LS bits shifted out are discarded. Unlike in LSR, the MS bits shifted in are the same as whatever the initial MS bit was, to preserve the sign in twos-comp numbers.
- ROR – Rotate Right. The bits are shifted some number of places down toward the least significant bit. The LS bits shifted out wrap around to become the MS bits shifted in.
- There’s also this: https://xkcd.com/2497/.
- BIND
- Berkeley Internet Name Domain (not Daemon). A popular open-source server suite for implementing DNS, the Internet’s host name-and-address lookup service. It uses a daemon called
named. It’s part of TCP/IP, and most of the 13 root DNS servers use it. Most ISPs rely on a BIND DNS server. BIND 9.2.3 was released in 10/2003. - BIOS
- Basic Input/Output System. The set of low-level startup routines stored in a ROM chip on a computer motherboard to run the POST, load the operating system into memory (see MBR), and provide standard program interfaces for hardware functions such as accepting keyboard input, displaying data on the monitor, and accessing disk drives. It’s customized for the processor hardware so that the operating system need not be. As of 2010, some motherboards are using UEFI instead of BIOS, a trend expected to grow.
- The BIOS relies on the 16-bit real mode of x86 processors, which can address just 1MB of memory. By convention, PC processors begin data execution at ROM address 0xFFFF0 – the last 16 bytes of that 1MB. The instruction stored there will be a jump to the actual ROM address of the BIOS code. In a DOS system bootup, the BIOS runs IO.SYS and MSDOS.SYS, which in turn initialize CONFIG.SYS, which activates COMMAND.COM, which calls AUTOEXEC.BAT. Most PCs load the BIOS code into main memory after bootup for quicker access, creating what’s called a shadow BIOS.
- The BIOS chip used to be EPROM, supplemented by a separate, non-volatile, battery-backed CMOS chip that stored user settings. The only way to change that type of BIOS was to physically replace the chip. Nowadays, an EEPROM or flash memory chip holds BIOS and user settings, and the user can replace or update the BIOS electronically with a BIOS-flashing utility.
- This feature comes with a downside: advanced malware with its own flashing tool can copy itself into a user-writeable BIOS, where it can escape detection and survive even the erasure of the hard drive. For years, such attacks were considered impractical due to the many different BIOS vendors and versions in use. Malware authors are beginning (2012) to find ways around this obstacle. Researchers have proposed several defenses, but the only sure one is to physically disable BIOS writes.
- BIPS
- Billions of Instructions Per Second.
- B-ISDN
- Broadband ISDN. See ISDN.
- BIST
- Built-In Self-Test. Same thing as BIT.
- BISYNC
- Binary Synchronous Communications. See data protocol.
- BIT
- Built-In Test. A test of functionality that a device performs on itself or on a subsystem. There are sub-types of BIT, distinguished by what triggers them: startup BIT (SBIT) or power-up BIT (PBIT), run when the device is first powered on; initiated BIT (IBIT) or commanded BIT (CBIT), run upon command from some outside source; periodic BIT (PBIT) or scheduled BIT (SBIT), which occurs at scheduled intervals; and event BIT (EBIT), in response to some operational event.
- Bitcoin
- The first of the cryptocurrencies, released in 2009 by someone using the pseudonym Satoshi Nakamoto. It’s an online, peer-to-peer (i.e., no controlling authority) virtual currency. Using it requires a sophisticated freeware program and an encrypted, constantly updated database called a blockchain that contains records of every bitcoin and every transaction.
- Users can mine new bitcoins by performing a long series of hashing computations that use SHA-256 encryption. The blockchain’s algorithm automatically adjusts the difficulty of these computations to keep the rate of block creation constant: one new block every 10 minutes. The first miner to complete the computations for a new block adds it to the end of the blockchain, a step referred to as proof of work. Once enough other users accept the addition, the miner claims some algorithmically determined number of bitcoins as a reward. The difficulty of mining each new block has risen dramatically since 2009 as more miners have gotten into the game, but so has the market price of a bitcoin.
- At first, bitcoin miners relied on standard PC microprocessors. As the computations became more difficult, and the race to be first for each block intensified, miners started repurposing GPUs for the task. The private bitcoin-mining companies that sprang up introduced cloudsourced mining, both legally and illegally, and ASICs designed specifically for bitcoin mining. By 2018, the computations had become so demanding that the worldwide mining of bitcoins was estimated to consume as much electricity as the entire nation of Iceland, and the value of new bitcoins was often less than the cost of the electricity used to mine them.
- Users exchange bitcoins with one another using encryption key pairs (one public and one private key) that the algorithm generates for them. Each user is known to others solely by their chosen pseudonym and associated public key, granting some degree of anonymity, and uses their private key to authenticate their transactions.
- Although individual users can have their private keys stolen, the blockchain itself has proved largely impervious to attack, because each new block incorporates the cryptographic hash of the block before it. To undetectably alter a block, an attacker would have to alter every subsequent block as well, which would mean redoing all of the computations.
- Non-anonymous brokers exchange bitcoins at market rates for standard currency. Each bitcoin is numbered and can be tracked, but the Darknet contains Bitcoin money-laundering services.
- Bitcoin has no governing body, and the algorithm code is public knowledge. If a user wants to change the algorithm, and the rest accept the change, it becomes the new version. However, if some users reject a change, the result is two incompatible versions with different user bases, each claiming to be the standard (a hard fork). As of 2022, this has already happened several times and is almost certain to happen again.
- bit interleaving
- See interleaving.
- bitmap
- A simple Microsoft/IBM image file format that defines a rectangular grid of pixels and specifies the color of each individual pixel. Color resolution is 1 (monochrome), 4, 8, 16, 24, or 32 bits per pixel. This is an inefficient way to represent color images, so the bitmap has given way to GIF, JPEG, and other, more complex standards. Bitmaps use the .bmp filename extension.
- BIU
- Bus Interface Unit. An integrated component of some microprocessors that controls data transfer to and from external devices.
- BJT
- Bipolar Junction Transistor. See transistor.
- blackbody
- An object that perfectly absorbs radiation, i.e., without reflection. This makes it a perfect radiator as well – any radiation coming from it is characteristic of the object’s composition & temperature, not of the incident radiation. Stars can be considered blackbodies. Also, see IR.
- black box
- (1)
- Any device whose inputs and outputs are known, but whose inner workings are unknown or irrelevant.
- (2)
- Popular name for data-collection systems used on commercial aircraft. See CVFDR.
- blade server
- A single-board computer (SBC) designed for use as a network server. A typical installation will host a number of hot-swappable blade servers in a rack-mount backplane enclosure.
- BLE
- Bluetooth Low Energy. A low-power alternative mode of Bluetooth.
- BLER
- Block Error Rate. The ratio of erroneous data blocks to total transmitted data blocks. Used instead of BER in assessing W-CDMA performance.
- blockchain
- Also called a distributed ledger. A type of smart database meant to be publicly shared, and potentially updated by any user, without the intervention of a controlling authority. It uses encryption to control and validate the updating process and ensure that all users have the latest version. Database entries are the blocks, with each new block incorporating a hash of the previous block and the encryption key of the user adding it. Hence the name.
- A blockchain is inherently slower and less private than older database models. A variant called the permissioned ledger partially offsets this by having a governing body of super-users with sole authority to make changes to the algorithm and grant or deny user access.
- Bitcoin, which is based on a blockchain, is what drew the IT world’s attention to the concept. Its success made blockchains a very hot subject, as well as inspiring countless other cryptocurrencies and eventually NFTs.
- block code
- See FEC.
- blog
- From “Web log”. A frequently updated personal Web site.
- Blue Lightning
- Under Intel, see 80486 SLC3 entry.
- Bluetooth
- Named for a 10th century Danish king who united Denmark and Norway, this Ericsson short-range wireless TDD technology introduced in 1999-2000 enables data devices to communicate autonomously in ad-hoc virtual networks. The Service Discovery Protocol (SDP) makes the connections, and the Logical Link Control and Adaptation Layer Protocol (L2CAP) makes them available to applications.
- Bluetooth uses 79 channels spaced 1 MHz apart in the 2400-2483.5 MHz ISM band, frequency-hopping through them at 1600 hops/second, or 625 µs dwell time. Its signal is GFSK with 350 kHz excursion and a full duplex data rate of 1 Mb/s (version 1.2 Basic Rate), 2-3 Mb/s (version 2.0 Enhanced Data Rate, or EDR), or 24 Mb/s (version 3.0 or later). Overhead eats up some of that – throughput is about 30% less.
- There are three classes for transmitter power level. Class 1 transmits at 100 mW and has nominal 100 m range; Class 2, 2.5 mW and 10 m; Class 3, 1 mW and 1 m. Actual range can be less, or much more, depending on conditions and data rate. Its reliance on unlicensed spectrum limits the legal broadcast range, but Bluetooth can operate over distances of miles using narrow-beam antennas.
- Up to eight devices (one master and seven slaves) can make up a single network, known as a piconet. If at least one device is also an access point (AP), the network can reach the telephone system and the Internet. A device can simultaneously connect to more than one piconet; a scatternet is an amalgam of independent, unsynchronized piconets linked by common members. Bluetooth competitors include 802.11b (Wi-Fi) and UWB.
- Bluetooth v4.0 (2010) adds a variant, Bluetooth Low Energy (BLE), also called Bluetooth Smart, which cuts power consumption by sending traffic in short bursts rather than continuous streams. It divides the same frequency band into 40 rather than 79 channels, each 2 MHz wide, still using GFSK modulation. Transmitter power is no more than 10 mW. It has about the same range as Bluetooth but much lower data rate, up to 270 kb/s throughput. It’s meant for applications where small size and low power are key.
- In June 2004, the first Bluetooth worm capable of infecting mobile phones appeared. For security reasons, turn off Bluetooth connections when they aren’t in use.
- Blu-ray
- Optical storage format intended to replace the DVD. It competed with the HD DVD format after a failed 2005 attempt at a compromise, but by 2008 was clearly the victor. It uses region codes (like the DVD), and AACS anti-copying technology.
- BMA
- Blind Mate. See cable connector.
- BME
- Base Metal Electrode. A technology for making multi-layer ceramic capacitors with non-precious metals, which are cheaper but have lower conductivity. Compare PME.
- BMI
- Brain-Machine Interface.
- .bmp
- See bitmap.
- BMP
- (1)
- Basic Multilingual Plane. Under data code, see UCS.
- (2)
- Bound Multi-Processing. See multiprocessing.
- BMS
- Battery Management System. A microcontroller-driven device that manages a rechargeable battery.
- BNC
- Bayonet Neill-Concelman. See cable connector.
- BNT
- Bayonet Neill Triaxial. See cable connector.
- BoB
- Breakout Box. A device used to provide external access to signals and voltage levels that exist inside some other device, for testing purposes.
- BOC
- Bell Operating Company. See divestiture.
- Bode plot
- Named for Bell Labs engineer Hendrik Wade Bode, usually pronounced BO-dee. A graph of a LTI system’s amplitude or phase response as a function of frequency.
- BOFH
- Bastard Operator From Hell. A network administrator with a hostile attitude, from a series of (originally) Usenet short stories by Simon Travaglia. Simon has moved them to the Web at http://bofharchive.com/.
- bolometer
- An 1878 (!) invention that measures radiant energy. A conducting element isolated from its surroundings absorbs radiation, and the resulting ΔT of this element is measured by any of several methods.
- Boltzmann’s constant
- Named for Austrian physicist Ludwig Boltzmann (1844-1906). The ratio, often represented as k or kB, of a molecule’s average energy to its Kelvin (K) temperature. Its value is approximately 1.38 × 10-23 [J/K], or –198.6 [dBm/K-Hz].
- Information theory has shown that the minimum energy released by the erasure of a single bit of data is [kB T ln(2)], where T is temperature. (See Maxwell’s demon.) At room temperature, that’s about 3 × 10-21 J.
- BOM
- Byte-Order Mark. An optional character at the beginning of a UTF-# or Unicode text file identifying the byte order (endianness) the file uses. Since byte order isn’t an issue for UTF-8, the only point of UTF-8 with BOM is to make clear that the file uses UTF rather than some other data code.
- Bomarc
- Boeing-Michigan Aerospace Research Center. A long-range anti-aircraft missile developed in the 1950s by Boeing with U. of Michigan’s MARC. Its intended role was knocking down Soviet nuclear bombers, relying on guidance from SAGE. It could be equipped with a small (~10 kT) nuclear warhead, so that even a “miss” could hit the target, or multiple targets.
- The Bomarc is not really germane to this site’s purpose, but it’s an iconic example of Cold-War technology: big, daring, bad-ass cool, and kind of insane in a way that made sense at the time.
- boolean
- For English mathematician George Boole (1815-1864). Having two logical states: 1/0, true/false, on/off, yes/no, up/down, high/low, etc. See binary logic.
- boost regulator
- See regulator.
- bootkit
- A type of malware that infects a computer’s boot process, enabling it to persist on the system. It’s usually but not always a rootkit as well.
- Bootp
- Bootstrap Protocol. A member of the TCP/IP protocol suite at the Application layer. Used for network PCs to enable them to boot over a network.
- bootstrap loader
- Named for the old adage about pulling one’s self up by one’s own bootstraps (in violation of Newtonian physics), the bootstrap loader (BSL) is a small program stored in the read-only memory of a system or individual processor, or the master boot record of a PC. The system BIOS or other startup process copies it into main memory and runs it when the system is powered on.
- A microprocessor BSL will typically initiate execution of stored code, or prepare to receive instructions from some external controller. A PC BSL finds the operating system in the system partition of the boot drive, loads it to main memory, and hands it the controls.
- BOP
- Bit-Oriented Protocol. See data protocol.
- boson
- Named for Indian physicist Satyendra Nath Bose (1894-1974), this is one of the two major classes of subatomic particles. The spin of a boson is an integer, and bosons can occupy the same space and quantum state. They include photons, mesons, pions, and certain atoms and nuclei. Compare fermion.
- bot
- From “robot”. A program that performs automated tasks over a network. Bots have benign uses, such as establishing chat connections, interacting with Web sites, crawling the Web to map sites for search engines, etc. They’re also used to spam social networks, disrupt online communities, automate harassment campaigns, and control malware-infected PCs.
- BOTEC
- Back-Of-The-Envelope Calculation. See WAG, SWAG, ROM.
- botnet
- A collection of network-connected devices all controlled by the same bot program, regardless of physical location. See malware.
- BPF
- Band Pass Filter. A filter that excludes frequencies above and below a particular range, but allows frequencies within the range to pass through.
- BPL
- Broadband over Power Lines. See PLC.
- BPON
- Broadband Passive Optical Network. See PON.
- bps
- Bits Per Second. Also b/s.
- BPSK
- Binary Phase Shift Keying. The simplest form of PSK, carrying one bit per symbol. The amplitude of a cosine waveform is multiplied by 1 for a bit value of 0, producing no phase shift, or -1 for a bit value of 1, producing a 180° (π radians) phase shift. (It can be done the other way.) Standard BPSK is received using coherent (maximum likelihood) detection, which employs matched filters.
- If the source data is differentially encoded, which avoids phase ambiguities but slightly increases BER, the receiver has the option to use the less complex differentially coherent detection, in which case the modulation is called D-BPSK.
- Bragg grating
- Named for British-Australian physicist William L. Bragg (1890-1971), whose 1912 Bragg’s law characterizes coherent and incoherent scattering of X-rays by the atoms of a crystalline lattice. The classic Bragg grating is an etched surface. It reflects a particular range of wavelengths while passing all others, so it serves as an optical band-stop or band-pass filter.
- A fiber Bragg grating (FBG) is a length of optical fiber with variations in its refractive index spaced at some interval Λ. (Exposing sections of the fiber to intense UV light creates the variations.) This gives the grating a specific Bragg wavelength λB that it strongly reflects according to the formula λB = 2neΛ, where ne is the effective refractive index of the grating. Certain environmental factors, notably temperature and strain, will alter ne, so the FBG can function as a sensor in addition to its obvious role as an in-line filter and switch for fiber-optic communications.
- brassboard
- A pre-prototype version of an electronic device, built to demonstrate the design.
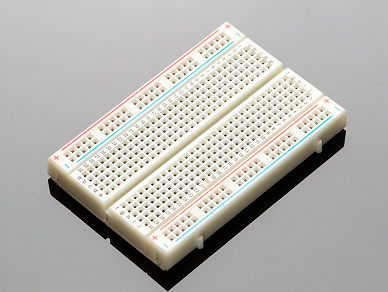
- breadboard
- A wiring board for connecting electronic components into basic circuits, to demonstrate or test a design. The name comes from the long-ago practice of assembling prototype circuits on actual wooden cutting boards.
- BRF
- Band Reject Filter. Same as BSF. See filter.
- BRI
- Basic Rate Interface. The basic 2B+D channel setup for ISDN.
- brick
- (v., trans.) To render non-functional, especially by a software change. Example: “Dude, your jailbreaking app totally bricked my iPhone.”
- Soft-bricking means the problem can be fixed by a reset, probably involving loss of data.
- bridge
- A device for connecting network segments that are running the same communications protocol. This permits increasing the size of a network without exceeding maximum cable length, device count, or repeater count. Unlike a router, a bridge uses MAC addresses (OSI layer 2), not protocol addresses (layer 3). This makes it faster, cheaper, and protocol-independent, but less capable.
- broadband
- A vague term for high-data-rate networking. Vendors started out calling a connection “broadband” if it carried at least 640 to 1024 kb/s. In 2010, the FCC defined it as at least 4 Mb/s, the minimum for standard TV video with MPEG-4 compression. In 2015, they updated that to a minimum 25 Mb/s downstream (provider to customer) and 3 Mb/s upstream, resisting calls from consumer organizations to aim higher and complaints from ISPs that even 25 Mb/s was too much. This means DSL is no longer considered a broadband connection, but a cable modem, at least on paper, is. In 2024, they raised it to a minimum 100 Mb/s downstream and 20 Mb/s upstream.
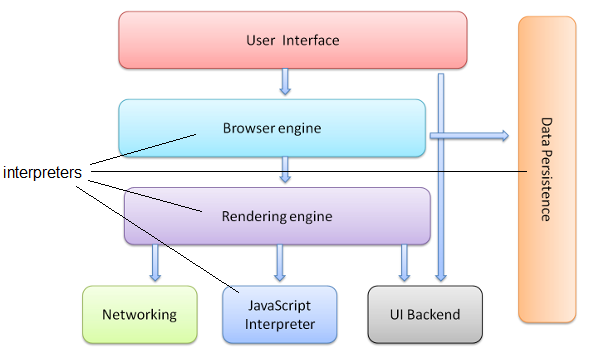
- browser
- A program that translates markup language code (e.g. HTML) into Web pages, and provides tools for navigating the World Wide Web. The first was Marc Andreesen’s NCSA Mosaic (1992).
- Text browsers with hyperlinks predate the Web, but “browser” has come to mean Web browser, with support for images, animation, sound, and video. Common Web browsers as of 2010 include Microsoft’s Internet Explorer, Mozilla’s Firefox, Google’s Chrome, Apple’s Safari, and Opera. These are general-purpose browsers; there are many others that are specialized for particular types of data.
- For security and privacy reasons, it’s a good idea to configure browsers to block third-party cookies and deny geolocation data. See also TLS.
- Modern browsers have a private browsing mode (Alphabet, Google’s parent company, calls it incognito mode) that prevents them from retaining browsing history or performing downloads, including of cookies and other tracking data from Web sites. It reduces the threat from some types of malware. In MS Windows, it’s activated by Ctrl-Shift-n for Google Chrome and Mozilla Firefox, or Ctrl-Shift-p for Microsoft Edge. In macOS, use Command-Shift-n or -p.
- b/s
- Bits per Second. Also bps.
- BSC
- Binary Symmetric Channel. From the field of information theory, this is a theoretical model of a discrete, memoryless physical channel with binary input and output sequences. Each input bit is reproduced at the channel output with a fixed probability of error [e], where 0.0 ≤ e ≤ 0.5, and a corresponding probability [1-e] of being correct. The worst case is total randomness: e = 0.5, or, in other words, a 50% bit error rate.
- BSD
- Berkeley Software Distribution. Originally, a version of Unix developed at the University of California at Berkeley. More recently, a family of free-software licenses, the first of which was created for BSD itself. Some of these licenses are supported by the FSF and the OSI.
- BSF
- Band Stop Filter. A filter that passes frequencies above and below a particular range, but excludes frequencies within that range. Also called notch, band gap, or band reject filter.
- BSL
- See bootstrap loader.
- BSoD
- Blue Screen of Death. The unrecoverable-error screen in some versions of Microsoft Windows.
- BSP
- Board Support Package. Manufacturer-provided software for an embedded processor circuit board, allowing programs compiled for the processor to use the board’s other hardware. It’s functionally a board-level device driver, and in fact commonly includes multiple drivers.
- BTC
- Short for Bitcoin.
- BTL
- Backplane Transceiver Logic. See logic family.
- BTU
- British Thermal Unit. A measure of heat energy. See power.
- BTX
- Balanced Technology Extended. Intel’s 2004 motherboard & PC chassis specification, intended to replace ATX. It didn’t. The smaller picoBTX (10.5" × 8") and microBTX boards are also little used.
- buck regulator
- See regulator.
- buckyball
- See fullerene.
- BUD
- Big Ugly Dish. Popular name for the 6½- to 12-foot, television-receive-only (TVRO) dish used beginning in the late 1970s to pick up the ~5 GHz C-band satellite feeds that carried analog FM TV signals to cable providers. They were most common in rural areas where cable didn’t reach.
- In the late 1980s, the providers began scrambling or encrypting their satellite feeds so that they could charge subscription fees for descramblers. Then, in the 1990s, they began to go digital (see DBS). By 2000, there wasn’t much left for the BUD to pick up.
- bus
- A multi-outlet signal pathway, usually but not exclusively in a PC. In terms of function, there are four bus types: data, address, control, and power. Power is often built into the other three types rather than laid out separately.
- There are short-range data bus standards such as ISA, VME, VLBus, SPI, I2C, PCI, and PCIe for use primarily within computing devices; and longer-range standards such as the ARINC family, CAN, Mil-Std-1553, RS-232, FireWire, and USB for interconnecting devices.
- Bus width is the number of data bits a bus can carry in parallel. When clock speed and number of bits are given for a microprocessor, they refer to its core bus – the data bus inside the chip itself, serving the execution units and L1 cache.
- The way the other bus types are used within PCs has changed over time, and the terminology is inconsistent to boot. For example, the terms internal bus and external bus should be avoided at the motherboard and system level, because they’re confusing; however, when referring to the microprocessor alone, they plainly mean its core bus and the bus connecting it to the motherboard, respectively. The bus types in a PC are, more or less:
- system bus (also front side bus, CPU bus, processor bus) – The data path from the CPU to the motherboard chipset. It terminates in a controller chip on the north bridge, and branches out to the rest of the system from there.
- In the mid-2000s, the traditional system bus was supplanted by faster, more complicated technologies: AMD’s HyperTransport and Intel’s QuickPath Interconnect (QPI), using memory controllers on the CPU rather than on the motherboard. This limits the CPU to just one type of memory, but avoids routing the memory bus through the overburdened system bus.
- Until the late 1980s, the system bus ran at core (processor) speed. With the 386 and 486, Intel and its rivals pushed it to 40, 50, and then 66 MHz to keep pace with the speed of the processors, but the motherboard chipsets of the time had trouble with this. The industry instead went for motherboards with system buses at some fraction of the core speed – half, one third, etc. The standard began at 33 MHz, increasing to 100 MHz by 2001.
- Some of the old hybrid processors (8/16-bit, 16/32-bit) also have different widths for their core and system buses. CPU computations are carried out on the wider internal path, and the narrower path is used to move data into and out of the CPU. This makes the motherboard cheaper, but slower. See 80386, 80486 under Intel.
- expansion bus (also I/O bus) – This is the bus users are most likely to be concerned with, because it provides motherboard slots for expansion cards. There are two general types:
- standard bus – The older type of expansion bus, traditionally 16-bit, 8.33 MHz ISA, although MCA and EISA also qualify. As high-quality graphics and other fast applications were developed, ISA became a bottleneck for PC peripherals. This inspired Compaq in 1987 to create the dual-bus concept, in which the standard bus is supplemented by a faster local bus. The standard bus gradually became irrelevant and disappeared.
- local bus – The newer type of expansion bus. Under a dual-bus architecture, a local bus controller linked to the system bus handles traffic for both the local bus and slower standard bus (which has its own subordinate controller). The first local buses were PCI and VLBus, both of which were 32-bit and ran at core speed. As core speed increased, the standards took different approaches. VLBus tried to keep pace, increasing to 50 MHz. PCI settled at a standard 33.3 MHz rate on early Pentiums, stipulating that the system bus would be some multiple of this. PCI was able to grow with the processors, while VLBus died off – it was designed for the 80486, and was too hard to change. The modern local bus, now (2010) PCIe, has replaced the standard bus entirely.
- address bus – The bus used by the CPU to address main memory (as opposed to carrying data to and from it, which is the task of the memory bus or, in older systems, the system bus). Other data buses have their own address bus, but this is the one everybody thinks of. Its bit width determines how much byte-addressable RAM the CPU can handle. Since the 80386 DX, the standard has been the 32-bit address bus, which can address 232 = 4,294,967,296 bytes (4 GB) of RAM. This capacity, once vast, is not sufficient for high-end systems as of 2007; address buses with functional widths up to 44 bits (244 = 16 TB) are on the market.
- memory bus – The bus between main memory and the memory controller. Until the 2000s, the memory controller was part of the motherboard chipset, accessed via the CPU bus. Newer systems put memory controllers on the CPU, so the memory bus goes straight from CPU to main memory.
- back side bus (also cache bus) – A 1998 idea from Intel for a separate bus from CPU to motherboard L2 cache, instead of accessing the L2 via the slower system bus. It runs at half or full core speed. It’s gone away as L2 cache has moved onto the CPU die.
- BW
- Bandwidth. Strictly, the size (in hertz) of the passband of a communications channel or signal. Used casually to refer to the rate of information flow over a channel or signal, since this figure is constrained by passband size, among other things.
- BYOD
- Bring Your Own Device. Refers to a task, event, or even a job that requires everyone to supply their own computing/networking resource, usually a smartphone, tablet PC, or notebook PC.
- byte
- A group of between 4 and 10 bits representing a single symbol or character. The octet, or 8-bit byte, is so ubiquitous that “byte” now means 8 bits unless otherwise stated.
- The SI standardizes a set of prefixes for powers of 1000: kilo means 103, mega is 106, giga is 109, etc. Hard drive capacity follows this rule, wherein 1 kilobyte (kB) = 103 bytes, 1 megabyte (MB) = 106 bytes, and so on with gigabyte (GB), terabyte (TB), petabyte (PB), exabyte (EB), zettabyte (ZB), and yottabyte (YB) – the latter being 1024 bytes, although there’s a long way to go before drives approach that size.
- When referring to computer memory, however, the SI prefixes have traditionally been used to mean powers of 1024, which is 210. That is, 1 kilobyte of memory is 210 = 1024 bytes; a megabyte is 1024 kB, or 220 = 1,048,576 bytes; and a gigabyte is 1024 MB, or 230 = 1,073,741,824 bytes. To end the confusion, industry groups since the late 1990s have been pushing the prefixes kibi, mibi, gibi, tebi, pebi, and exbi for such binary-based values. That’s why some sources talk about kibibytes (KiB), mibibytes (MiB), or gibibytes (GiB) of memory without sounding at all silly.





| a | b | a AND b | a OR b | a NAND b | a NOR b | a XOR b | a XNOR b |
| 0 | 0 | 0 | 0 | 1 | 1 | 0 | 1 |
| 0 | 1 | 0 | 1 | 1 | 0 | 1 | 0 |
| 1 | 0 | 0 | 1 | 1 | 0 | 1 | 0 |
| 1 | 1 | 1 | 1 | 0 | 0 | 0 | 1 |
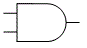
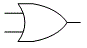
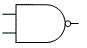
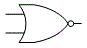
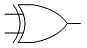
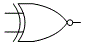
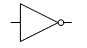
Binary logic gate symbols







Browser icons